Introduction
Web applications are everywhere. Developers are creating new technologies at a breakneck pace, and start-ups are being created overnight with new web services. Every application is different, and because the technologies used are so diverse, it can be difficult to automate any sort of web application assessment. However many tools exist to discover hidden domains, forgotten configuration files, common vulnerabilities and even download application source code without ever walking the application. This article will dive into some of these tools that can help in your own application audit.
Intercepting Proxies
When beginning to audit a web application it’s important to keep a record of what requests are being made while using the app. Often times applications will call functions server side without the user ever seeing the result exact result of these requests, such as API calls. This is where an intercepting proxy that logs your requests becomes an invaluable tool. Using Portswigger’s Burpsuite (Burp) or OWASP’s ZAP allow you to keep detailed information about your browser session and tamper with request data that was previously inaccessible through the front end. Both ZAP and Burp also create a nice directory tree-like structure for the application and passively scan your logs for potential vulnerabilities.
Subdomain Discovery

Sublist3r is a subdomain discovery tool that aggregates data from multiple search engines and brute forces subdomains in one run.
Subdomains are an often overlooked part of the assessment process. Too often you will find odd subdomains of large companies forgotten and overlooked, yet still in scope and vulnerable to a variety of attacks. One such example of this was in 2014 when Yahoo’s mx.horoscopo.yahoo.net domain was found to have an unauthenticated, unrestricted file uploader which allowed the attacker to gain remote code execution.
One of our favorite tools to discover these forgotten domains is “Sublist3r”. Sublist3r discovers subdomains using search engines such as Google, Yahoo, Bing, Baido, Ask, Netcraft and DNSdumpster. It also integrates the ability of “subbrute” to brute force subdomains using a wordlist to give you one of the most powerful subdomain discovery tools out there.
The Network Mapper (Nmap)

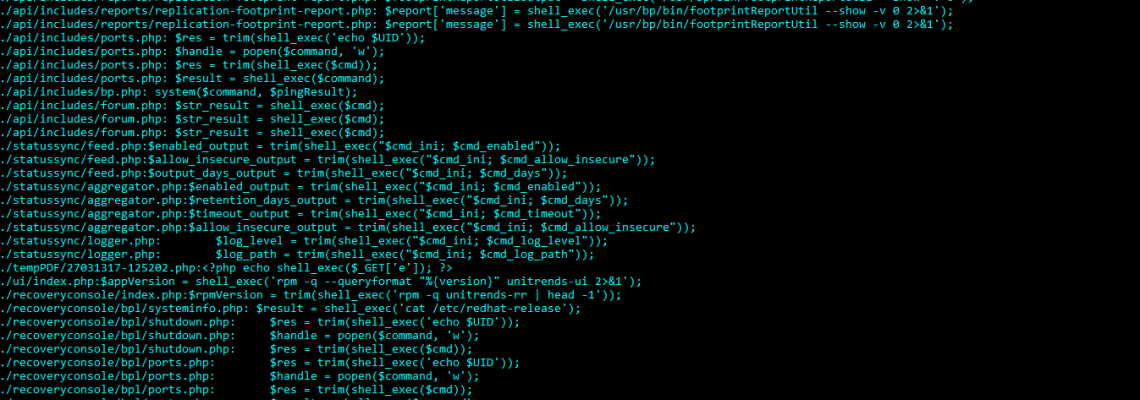
The output of running Nmap utilizing the scripting engine with an http-vulnerability script.
Nmap is a tool every security consultant is familiar with. It helps map network architecture, discover open ports, helps enumerate service information and more. While it may seem non-obvious why you would scan a web host with Nmap, but the reason being is that you must cover all your bases. You never know when there’s another hidden web application on a port outside of 80 and 443 that could compromise a web server, such as an administrator panel using default credentials. Another great example of this is an unsecured Elastic Search installation, a popular tool to expedite retrieval of data in a website, which could lead to remote code execution.
Also worth mentioning is the Nmap Scripting Engine (NSE). Nmap has an active community of developers that create different scripts to test for vulnerabilities during the program’s runtime. To run one or multiple scripts during the runtime of Nmap, all that’s needed is to provide the “–script” flag along with the name of the script, a comma separated list of scripts or using the glob syntax (i.e. http-vuln*). Many scripts come preinstalled with Nmap, but to download the newest scripts available you’ll have to visit the NSE webpage here.
Architecture Information
Once we have collected every webserver to audit and noted each port running a web server, we can begin analyzing the infrastructure of the web server. There are several ways to discover what language or content management system (CMS) is running in the backend, but one browser addon that compiles much of these techniques is Wappalyzer. Wappalyzer can even detect eCommerce platforms and JavaScript frameworks that are being loaded. Information is what allows you to chart your next course of action and how to proceed with tampering data.

Wappalyzer automatically analyzes applications as you browse, giving you information on the architecture of the web server.
CMS Scanning

JoomlaVS is a Joomla content scanner that enumerates outdated plugins against their security advisory warnings, much in the same way WPScan does.
Architecture information is tantamount as it gives direction on how to next assess the web server. If a well-known CMS like Joomla or WordPress is encountered, then we’d want to discover the version its running, installed modules and more to cross reference with the many vulnerabilities that riddle these frameworks. Recently during an audit, we discovered a Joomla webserver for a public health institution. Using JoomlaVs, we were able to quickly enumerate several vulnerable plugins which contained SQL injection and remote code execution. Other great CMS scanners include WPScan, Droopescan and CMSmap.
Directory Enumeration

Much like web servers hiding on non-standard ports, web applications can often have hidden functionality and directories that one would never discover through their normal or intended use. In rare cases you may have to build your own directory enumeration tool, but the majority of the time “dirb” does just fine. Dirb is a fast, simple and intelligent directory enumeration tool that attempts to discover vulnerabilities not covered by classic scanners. Configuration files, administrative panels and source code could all be discovered by this type of brute forcing. It should be noted that like any brute force attempt, you will only be as effective as your wordlist.
Outside of the default wordlist Dirb uses, we’ve personally used the wordlists in SecLists to great success. SecLists is a compilation of discovery, fuzzing and password wordlists to use when auditing an application. For wordlists related to directory discovery, wordlists be as broad as the top 1,000 disallowed entries in robots.txt across the web, to specialized lists relating to a particular architecture. Recently we used a wordlist from this repository to discover a forgotten SMTP page, which allowed us to send arbitrary mail from the application and discover the host’s IP address even though the server was protected by CloudFlare. Obscurity is not security, and through directory discovery we can rest assured we are not missing any low hanging fruit.
Note: If you’re looking for a password generator based on the keywords in a website, look no further than CeWL. CeWL scrapes a web application for interesting words and generates a password list for later use. You can often use this along with Hashcat (as seen in the WPA article) to create a strong, company specific password list.
DVCS-Ripper

DVCS-Ripper allows you to take publicly accessible version control systems, like GIT and SVN, and download different commits and updates from the repository. Above shows downloading the application source from a “.git” directory.
Web applications are not developed over night. Developers use all sorts of version control systems (VCS) to keep a centralized source for their application’s code base. However when a developer clones their repository into their new web server, hidden directories related to their VCS is created to keep track of updates, new commits and configuration settings. Since these hidden directories are often under the same directory where the application is running, these directories are publicly accessible over the web.
DVCS-Ripper is a suite of tools developed in perl that can discover and download web accessible version control systems, including GIT, SVN, Mercurial and more. DVCS-Ripper will crawl this structure and download all the files found. Repository names, usernames, and even source code can all be fetched from these hidden directories facilitating the total compromise of an application.
Closing
These tools only provide the introduction to the methodology used when beginning a web application audit. In this article alone, over ten tools are listed to help automate much of the initial scoping of a target. It’s up to an auditor to interpret the results of these tools and how they can be further leveraged in compromising an application.