RSA is a major information security conference in San Francisco every spring. With a tagline of “where the world talks security”, RSA is the epicenter of new infosec technologies. Yet despite the tagline, the security of the conference itself leaves attendees exposed. Through the normal registration process, Rhino Security Labs researchers identified vulnerabilities allowing an attacker to enumerate attendee email addresses.
While creating an account for the RSA Conference 2017, we ran across a common problem for accounts used only once a year – a password was lost. In attempting to recover the password for an outdated account, we ran across another common issue – the account we believe was used was incorrect.
Getting into things
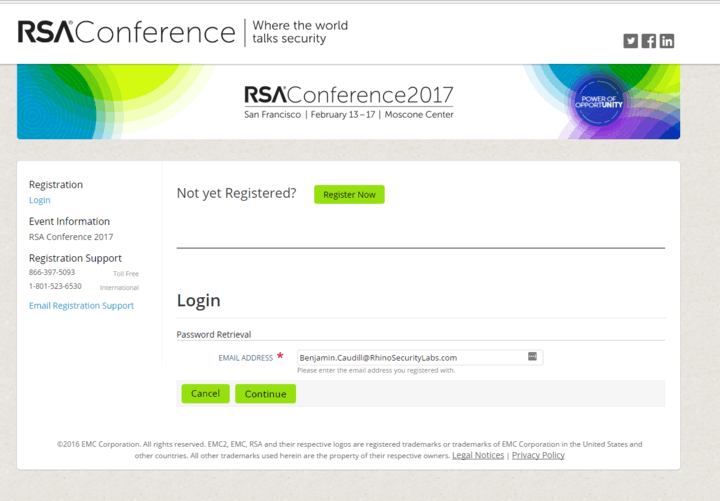
Unfortunately in this case, that led to an information leakage issue, exposing that information on the site. The user is shown as not being in the registered list, thereby confirming the email of all users not appearing with this same error message.

Keeping this in mind, we sent the same request through Burpsuite (a local proxy) and captured it to look at the POST data.

With no other parameters but the email address, this definitely looks like we can fuzz the value of email address, comparing differences in the HTTP responses. Burp makes this extremely easy by providing a module called Intruder, allowing for manipulating of specific strings within HTTP Request data.
Repeating these same packets with different “email” POST fields, we get the following results:
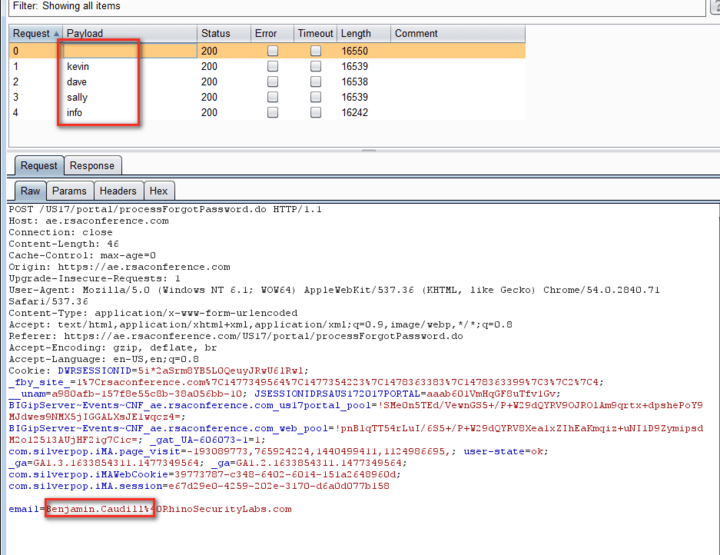
Surprisingly, four invalid requests didn’t create any kind of lockout, and as soon as the valid email address (info@rhinosecuritylabs.com) was provided, the HTTP Response confirmed that the account and that it’s been “…found and the password reset”.

This shows how easy it is to enumerate email addresses that have been used to register for the RSA Security conference. While this is a risk in itself, the bigger concern is how even the most robust security organizations – such as infosec conferences – often miss vulnerabilities which undermine their security posture
Thanks goes out to those at the RSA conference, who were quick to communicate and remediate the vulnerabilities listed above, and handled the issues in a prompt and professional manner.