Introduction: SQL Injection and Burpsuite
Burpsuite is the de facto standard of web application auditing tools, simplifying the discovery and exploitation of application vulnerabilities. Burp’s “Active Scanner” identifies a range of application flaws – from missing security headers to SQL injection – but the wide coverage leads to less depth in a single vulnerability type. In this blog post we look at SQL Injection as one of those areas.
In one instance, Burp missed SQL injection at two different injection points in the target app, only discovered later through manual analysis. This was later validated through SQLMap, which began retrieving database contents.
But as effective as it is, SQLmap comes at the expense of time. The sheer volume of requests can make SQLMap an infeasible option, taking hours – or even days — to fully enumerate an entire site for injection issues.
To give the depth of SQL injection testing that SQLMap offers, while reducing the time to scan, we created SleuthQL.
What is SleuthQL?
SleuthQL aims to augment an assessor’s ability to discover SQL injection points by automating some of the request analysis required during a web application assessment. SleuthQL is a Python 3 script to search Burp Suite’s request history for parameters and values that match syntax matching that of database languages, such as SQL.
It judges a parameter or value based on whether it matches a regular expression associated with database queries. SleuthQL can scan json, xml, form-data and url-encoded data without issue.
These regex matches include database names, common operands, common variable names and more. Once a match is discovered, it will create a list of vulnerable parameters per endpoint and per method the endpoint was requested with. Once this list is compiled, it will then iterate over all requests matching that endpoint and method, appending a custom injection marker (*) at the point of each potentially vulnerable parameter. It then writes this request out to a directory matching the domain name. You could then feed every request file in that directory into SQLmap for processing with the following command:
find $domainName -name “*.txt” -exec sqlmap -r {} –batch \;
If terminal output is preferred, it also prints each path and method that is vulnerable, followed by a list of variable names for an assessor to manually investigate by hand.
Download and readme for SleuthQL are available here.
What does SleuthQL not do?
Currently, there are a few limitations of the tool, such as parsing of nested parameters of different types. For example, there have been instances where JSON POST data is sent to an application with parameter values that are base-64 encoded. That value would not be able to be parsed by SleuthQL and would require an expert’s eye.
Moreover, it does not scan an application’s cookies for potential injection points. This is because cookies often interfere with session state (and invalidate the current session), and have a particularly high number of false positives, such as CDN identifiers.
Using SleuthQL
To generate your Burp XML required of SleuthQL, simply highlight all the items within your scope under the Target -> Site map pane, or highlight every item in your Proxy -> HTTP History tab, and click “Save Items.”
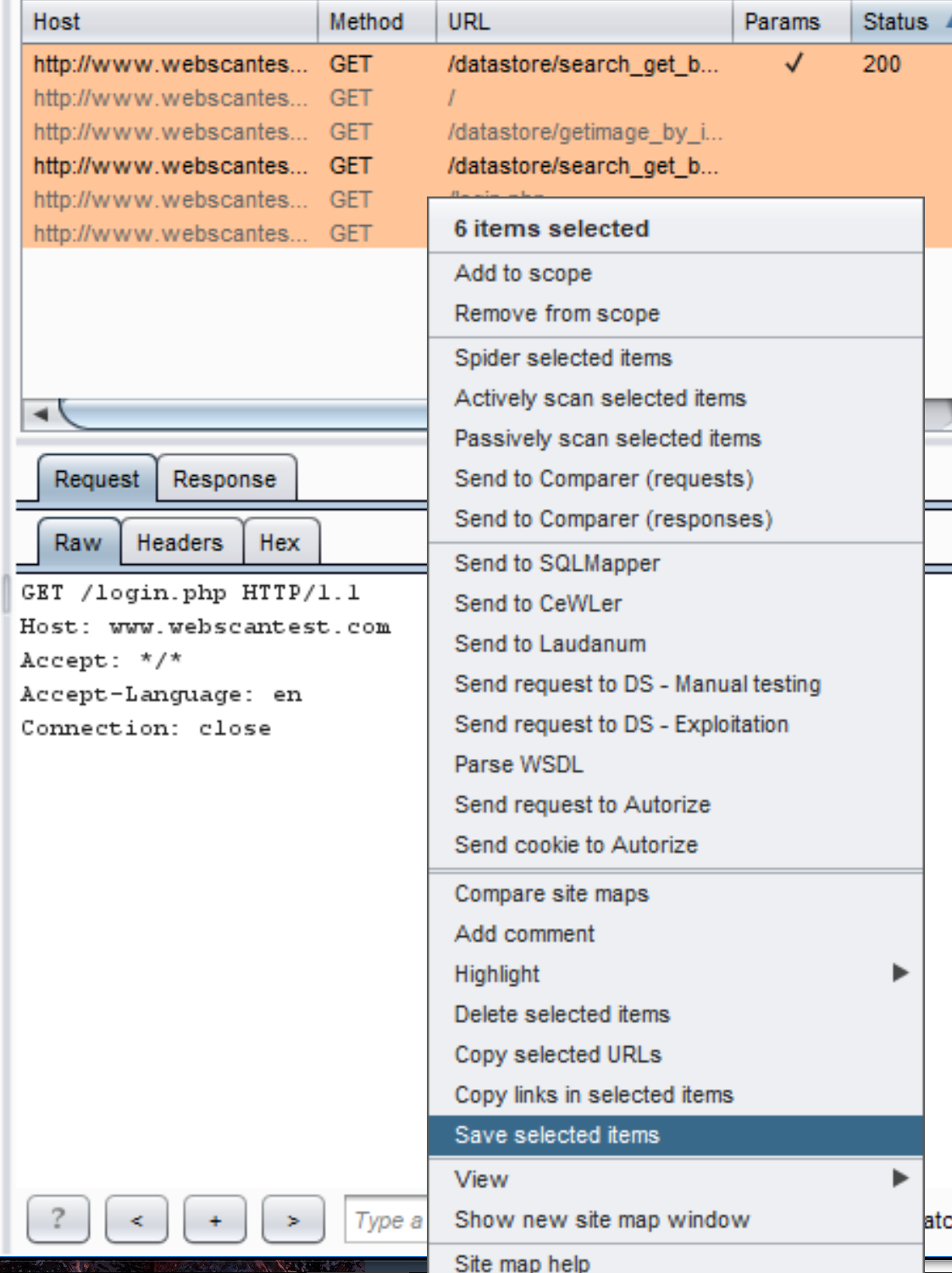
Saving items from Burp’s Proxy -> HTTP history tab.
Once the XML has been generated, simply pass a comma-separated list of domains to SleuthQL via the -d option, along with the file path to the Burp XML with -f. SleuthQL then creates a short list of potentially vulnerable endpoints, creates the request files required by SQLmap, which at that point the assessor can simply let the tool run on endpoints they would have discovered through manual analysis. If SQLMap were to detect a potential injection point, the assessor could simply comb through the contents of the ~/.sqlmap/$domain/session.log file for any successful injections. The tool could even be expanded upon by refining the regexes within the settings.py file or changing them altogether to, for example, search for deserialization vulnerabilities.
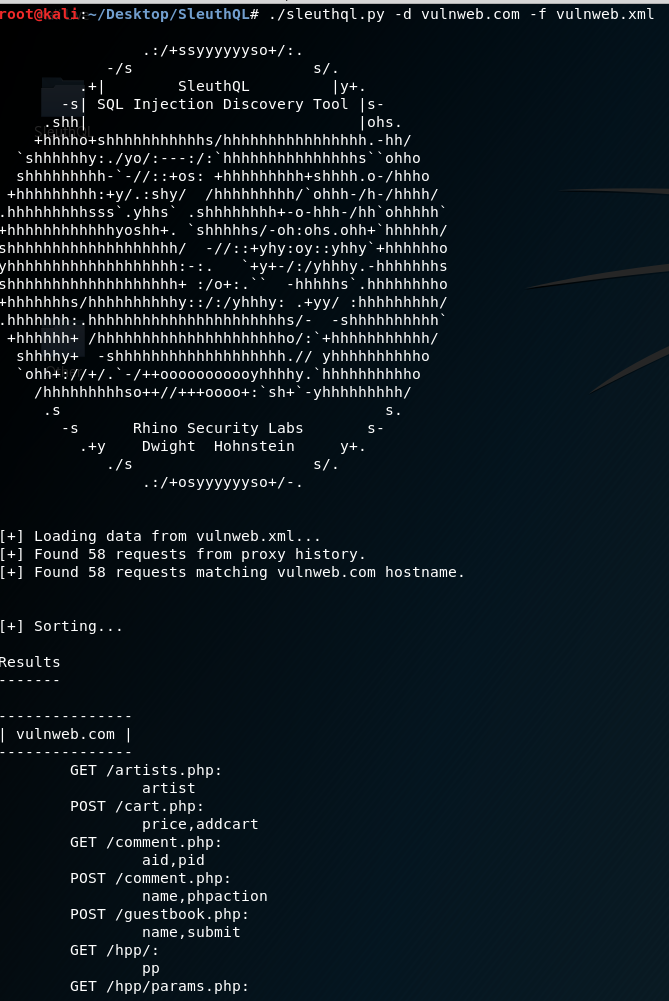
An example run of SleuthQL on vulnweb.com, showing that it identified the above parameters as being potentially vulnerable.
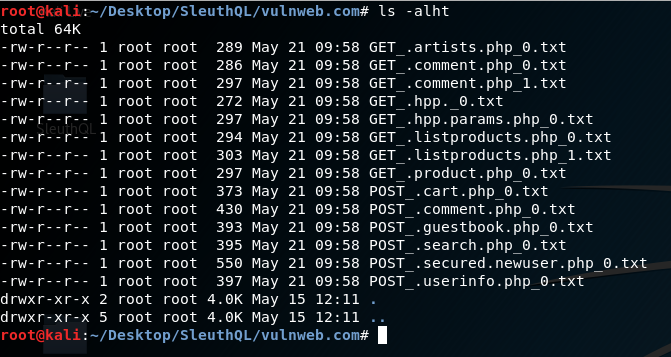
The generated request files from the Burp Proxy history, with injection markers for each vulnerable parameter within them.
Video Walkthrough
Conclusion
In conclusion, SleuthQL aims to discover potentially vulnerable SQL injection points in web applications by parsing parameter names and values for potentially dangerous values. Using this in tandem with a tool like SQLMap can help augment a regular application audit and ensure a total depth of coverage.
You can download SleuthQL from the Rhino Security Labs Github.



