Intro: A Standalone Tool and Improving Pacu
While performing AWS penetration tests, we’ve repeatedly encountered a need for a tool to manually review and audit IAM permission policies. IAM Permissions can be spread out over multiple inline and managed policies, contain duplicate permissions, and include any number of permissions logic combinations making manual review a grueling task. When it comes to looking for privilege escalation in these permissions, although Pacu and its privilege escalation scanning module are effective, it can often miss certain escalation pathways. These routes may involve complex factors like distributed permissions across multiple Roles accessible to an attacker, which aren’t readily detected by scans out of the box.
To address this, we sought a tool that helps fill these gaps and could be integrated with Pacu to streamline the querying of enumerated IAM permissions. This led us to develop a standalone tool – IAMActionHunter – as well as a Pacu module with similar functionality (iam__enum_action_query).
This blog introduces each tool and provides examples of their potential utility along with some basic examples.
Note: If you just want to start using the tools, skip down to “Getting Started With..”.
Offensive and Defensive Use Cases
The standalone IAMActionHunter can be utilized by both offensive and defensive security teams.
For offensive security, IAMActionHunter can be used to search for potential privilege escalation opportunities in AWS accounts by querying various AWS IAM permissions that might be exploited. While other tools perform scans to identify privilege escalation risks, this tool enables a more manual approach, allowing users to investigate any permission they choose and quickly assess the roles, users, and resources they apply to for targeted analysis or privilege escalation path idea generation.
For defensive security (Blue Team), this tool offers the ability to output and save query results in a CSV format, which is beneficial for security teams seeking a quick high-level overview of principal permissions and the resources to which they apply within an AWS account. For instance, you may want to identify users and roles with iam:put* permissions in an account. By executing a query and generating a CSV, you can easily review all users and roles with these permissions, along with the resources they have access to.
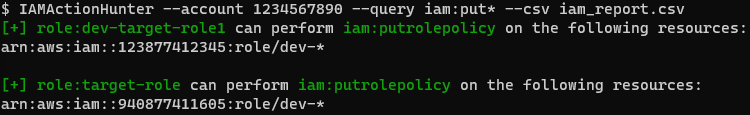
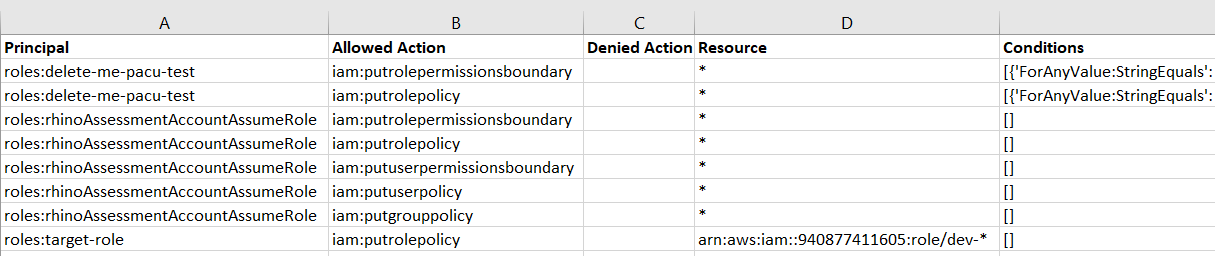
The CSV Output for Analysis
Example Use Cases
IAMActionHunter (Standalone)
Here’s a basic but practical example illustrating how IAMActionHunter can be used for identifying AWS privilege escalation vulnerabilities when permissions are spread across multiple principals.
If we have 2 Roles in an AWS environment that aren’t individually vulnerable to privilege escalation, but are a risk when combining them together. These roles both permit “iam:putrolepolicy” and “iam:createrole” actions separately, but only for a specific resource with a “dev-*” prefix.
Inline policy of dev-target-role1:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:putrolepolicy",
“sts:assumerole”
],
"Resource": "arn:aws:iam::123877412345:role/dev-*"
}
]
}
Inline policy of dev-target-role2:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:createrole"
],
"Resource": "arn:aws:iam::123877412345:role/dev-*"
}
]
}
Some IAM privilege escalation scanning tools might not detect this vulnerability as they typically search for high-risk actions that apply to all resources (“*”) and only take into account if all the needed permissions apply to a single role.
However, a manual review of the policies would reveal the potential for privilege escalation, exploiting this with the following steps:
- Assume the dev-target-role2.
- Create a role named “dev-anything”.
- Add a trust policy that allows you to assume it.
- Switch back to dev-target-role1.
- Put an inline policy on the new role that grants you the desired permissions.
- Assume the new “dev-anything” role you created.
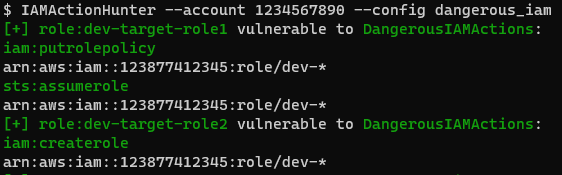
By using IAMActionHunter, you can uncover such vulnerabilities through manual queries or predefined configurations. The image below shows an example of using a configuration to look for dangerous IAM actions.
This reveals all the resources and permissions needed to perform the escalation described above.
New Pacu Module - iam__enum_action_query
Using the iam__enum_action_query module in Pacu makes it easier to investigate findings from Pacu to determine if privilege escalation paths are possible, drilling down into other Principals and permissions.
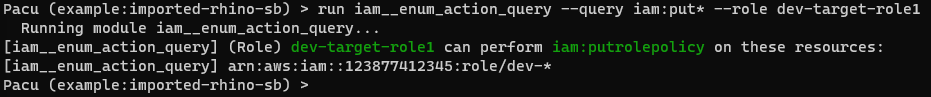
Here you can see a finding from the existing iam_privesc_scan module in Pacu. This output is stating that the “dev-target-role1” is vulnerable to Pacu’s “PutRolePolicy” escalation method. But Pacu’s output does not show any information about the actual permission policy which makes it vulnerable and to which resources the permissions apply.

Here you can see a findings from the iam_privesc_scan module in Pacu.
To query information about the policy and the affected permissions you can now use iam__enum_action_query to view the permissions and resources associated with this without having to manually analyze a JSON blob.
Getting Started With IAMActionHunter
Getting Started with the ‘iam__enum_action_query’ Pacu Module
As a standalone tool, IAMActionHunter is easy to set up and use. To get started, clone the IAMActionHunter repository and set up following the readme. Once installed, you can collect IAM information for users and roles and run queries on the collected data.
With IAMActionHunter, you can query specific IAM permissions, use wildcards, filter by Role or User, and output results to a CSV file for further analysis. You can also run and create config queries using a JSON configuration file, or combine multiple actions using the –all-or-none option to show results only if a user or role is allowed to perform all queried actions.
Much of the functionality of IAMActionHunter has also been integrated into Pacu, Rhino’s popular AWS exploitation framework, as a new module.
Simply update Pacu to the latest version and run the iam__enum_action_query module to query IAM permissions in the same format.
Conclusion
IAMActionHunter provides another tool in the process of hunting for privilege escalation in AWS accounts when manual review of policies is required. By using IAMActionHunter (or its associated Pacu module), you can uncover potential risks and vulnerabilities in your AWS environment, allowing you to take a more proactive approach to securing your cloud infrastructure.
Whether you are a cloud pentester looking to find privilege escalation opportunities, or a defensive security team member wanting a high-level overview of permissions and resources, we hope you find IAMActionHunter or Pacu’s iam__enum_action_query helpful.
To learn more about IAMActionHunter and how to get started, visit the GitHub repository at https://github.com/RhinoSecurityLabs/IAMActionHunter.
To try out the new Pacu module, check out the Pacu GitHub repository at https://github.com/RhinoSecurityLabs/pacu.
As always, feel free to follow us on Twitter for more releases and blog posts: @RhinoSecurity, @daveysec, and chat with us on Discord: https://discord.gg/8vFE7ucx9W
Lastly, a big shout out to the Netflix-Skunkworks team and their commitment to open-sourcing AWS security tools.
Both IAMActionHunter and its Pacu equivalent iam__enum_action_query use https://github.com/Netflix-Skunkworks/policyuniverse to parse AWS Policy Sstatements in an accurate manner, a big help in creating these tools.



