Pritunl Vulnerability Overview
Affected Product Summary
The Pritunl VPN Client service is vulnerable to an arbitrary file write as SYSTEM on Windows. This is due to insecure directory permissions on the Pritunl ProgramData folder. The arbitrary file write is then able to be leveraged for full privilege escalation due to the privileged Pritunl VPN service executing commands as SYSTEM without specifying the full path of the executable.
The impact is elevation of privileges to SYSTEM on Windows.
Vendor: Pritunl
Product: Pritunl VPN Client
Confirmed Vulnerable Version: 1.2.3019.52
Fixed Version: 1.2.3019.52a
Product Link: https://client.pritunl.com/#install
Confirmed Vulnerable Platforms: Windows
What is Pritunl VPN?
Pritunl is a distributed VPN server that allows enterprises to to connect their datacenters and multiple cloud environments with site-to-site links and remote user access. Being open-source, its a common option for companies looking for OpenVPN compatibility but with greater scale and cloud compatibility.
Connecting to a Pritunl VPN provides some options. While the server page notes “all OpenVPN clients are supported”, additional integration is offered in using the Pritunl OpenVPN client as well.
Security is at the forefront of the application as well. On its Security page, Pritunl describes itself as “the most secure VPN server available”, and promotes its open-source codebase as the only means to “guarantee the security of your network.”
As pentesters, we’ve come across Pritunl several times, most often in connecting AWS/GCP/Azure cloud environments together.
Arbitrary File Write As SYSTEM Technical Details
After a user imports a VPN configuration file into the Pritunl VPN Client, a file is written to “%APPDATA%\pritunl\profiles\[profile_ID].ovpn”. When a user attempts to connect to the profile, the VPN configuration file is sanitized of dangerous OpenVPN directives and then written to “%PROGRAMDATA%\Pritunl\[profile_ID].ovpn” by the Pritunl VPN service. Once the file is written, the Pritunl VPN service acts as a wrapper to the openvpn.exe executable and executes OpenVPN as SYSTEM, supplying the sanitized configuration file in the “–config” argument.
Since it is possible for any user to create new files in %PROGRAMDATA%\Pritunl\* by default, it is possible to continuously write a configuration file containing dangerous OpenVPN directives to this directory with a matching profile ID and upon attempting to connect to the profile the Pritunl VPN service will eventually execute openvpn.exe with the modified profile.

Even though openvpn.exe is executed with the “–security-script 1” flag, preventing external commands from being executed, this still allows the “log” OpenVPN directive to be used which writes the log output to any specified file as SYSTEM and it is possible to control partial contents of the log output.
After importing a profile named “privesc”, this can be done with the following PowerShell command and repeatedly clicking “connect” on the privesc profile while the loop runs.
$profile_id = ((Select-String '{"name":"privesc"' $env:APPDATA\pritunl\profiles\*).filename).split('.')[0]; while (1){"client`ntls-client`ndev TUN`nlog `"C:\\Program Files (x86)\\Pritunl\\ipconfig.bat`"`nauth-user-pass`nca `"INJECTED CONTENT`"" | Add-Content "C:\ProgramData\Pritunl\$profile_id"}
Leveraging the File Write For Full Privilege Escalation
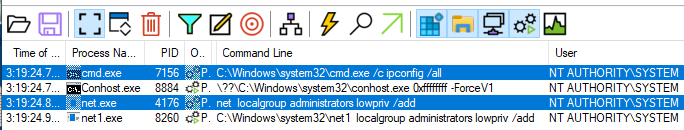
The arbitrary file write as SYSTEM can be leveraged to gain command execution as SYSTEM in the following way.
Each time a connection attempt is made using Pritunl VPN Client the “ipconfig” command is called by the Pritunl VPN service running as SYSTEM. The command line to execute “ipconfig” is done without specifying the full path of the executable. Because this command is executed from the working directory of “C:\Program Files {x86)\Pritunl\” it is possible to use the arbitrary file write vulnerability above to write commands into “C:\Program Files {x86)\Pritunl\ipconfig.bat”. This Batch file will then be executed as SYSTEM by attempting to connect again using the Pritunl VPN client.

Conclusion
Disclosure Timeline
While this is one of many findings we have in VPN clients (more to be released soon), this is the only one that’s open source.
This is also a good reminder that while open source software certainly offers transparency benefits, its not a panacea for security.
Acknowledgements to Zachary Huff and the Pritunl team for the quick patch upon disclosure.
| 2/17/2022 | Reported to Pritunl |
| 2/17/2022 | Vendor fix committed to the GitHub repository |
| 3/29/2022 | Pritunl Client v1.2.3019.52a released and announced by vendor. |
| 4/5/2022 | Full Disclosure (blog post) released |