Intro to EVGA Precision X1
Precision X1 is a software overclocking tool released by EVGA. This tool allows users to overclock their GPU, aka graphics processing unit or graphics card, to eke out more performance in video games or other applications.
One of the features that Precision X1 offers is the ability to perform auto-updates, so users can know when a new version is available. As a penetration tester and user of the software myself, my curiosity was piqued when I saw that this was a feature. When performing penetration tests, auto-updating features are always of interest, so I decided to look into how it all worked and uncovered a critical chained vulnerability in the auto-update mechanism.
Vulnerability 1: Insecure Updater
When Precision X1 checks if a new version exists, it downloads a file off of EVGA’s web server: https://www.evga.com/precisionx1/px1update.txt. This file contains metadata about the current update, including current version, a download link to download the executable installer, and a “product URL” which leads you to the Precision X1 product page.
To start the update process, Precision X1 will check their current version against your current version, and if there is a discrepancy, it will open the product URL in your default web browser to download the new version.
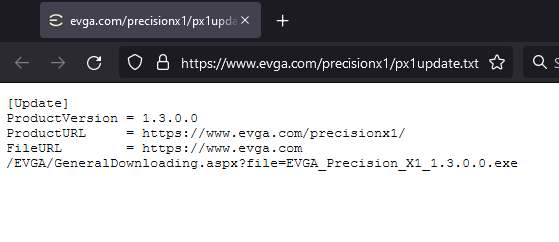
Metadata Example
The vulnerability here is that, prior to Precision X1 1.2.6.0, this file was downloaded over plaintext HTTP rather than HTTPS. This is problematic because an attacker can leverage this in a number of ways – a malicious DNS server at a LAN party pointing www.evga.com to their own web server or a traditional man-in-the-middle attack, just to name a few.
If the attacker can modify this update metadata, the logical attack path is that they can modify the URL of the executable that is listed and Precision X1 will download and execute it, right?
Chaining Vulnerabilities for RCE
Well, it turns out this does not work! Precision X1 is not capable of auto-downloading and installing the executable. Instead, it opens your web browser to the URL that is defined as the product URL, and you still must manually download the new version yourself. The auto-updater in this case is more like a new version notifier.
That said, one should always look deeper into how things work. Even though it is not obvious at first, it is still possible to leverage this vulnerability into obtaining full RCE on the victim’s machine. Let’s dig a bit deeper into the code and see how that is possible.
Vulnerability 2: Command Injection
Precision X1 is an application built in .NET and was not obfuscated by EVGA, meaning that we can cleanly decompile the application into what is essentially it’s original source code. This allows us to look at what is happening under-the-hood, and analyze things more deeply. Let’s take a look at what happens when Precision X1 parses the update metadata.
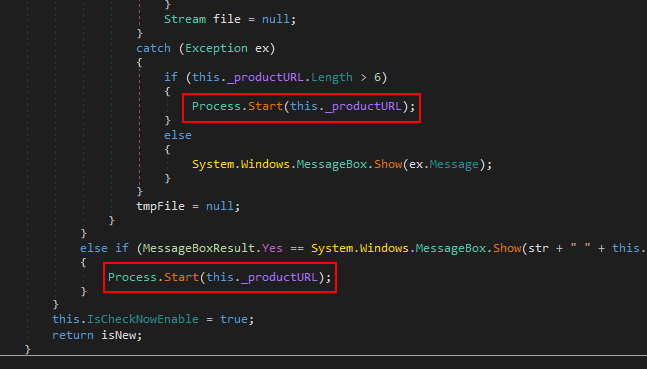
Decompiled Code with Call to Process.Start
As you can see, the value of the product URL from the metadata is passed, unsanitized, into .NET’s Process.Start() function. This function, when passed a URL, will simply open the user’s default web browser to that URL. No problem, right?
Well, Process.Start() is also the function in .NET to spawn new processes. This means that if the product URL is replaced with the name of an application, such as calc.exe, Calculator will be started whenever the user accepts the auto-update prompt. This could easily be substituted with a more dangerous payload, such as one that downloads and runs an executable, directly leading to full and arbitrary RCE.
CVE-2021-41577: PoC Exploit Video
To demonstrate this, here is a short clip of what happens when you replace the product URL with calc.exe which will open the Calculator.
Conclusion
This vulnerability impacts any version number less than 1.2.60. If you are on an older version, it is advised that you update immediately. If you are using the Steam release of Precision X1, you’ve likely had the updated (fixed) version, which was released in September 2021.
I would like to thank EVGA for their prompt turnaround in fixing this issue. Working with their security team was a pleasure, and I look forward to working with them again if I find more vulnerabilities in EVGA products in the future.
Disclosure & Remediation Timeline
– 08/24/21: Reported vulnerability to EVGA
– 09/02/21: EVGA reports that the vulnerability is remediated and asked me to test a fix
– 09/02/21: I test the fix and report that it is remediated properly
– 09/07/21: EVGA publicly releases Precision X1 1.2.60 which contains the fix
I hope you enjoyed reading my writeup of this issue. It was fun to investigate and also a good example of why one should always thoroughly dig into potential things more to see if they can’t be leveraged into a more pivotal finding. If I had given up and assumed that being able to modify the auto-update metadata could not be maliciously abused, I never would’ve uncovered the true potential impact of this issue.
Follow us on Twitter to stay up-to-date with what we’re doing and our future research. We can be found @RhinoSecurity and I personally can be found @hun10sta. Thank you for reading!