Vulnerability Overview
Affected Product
Forticlient is Fortinet’s basic VPN client which offers SSL VPN and IPSecVPN VPN connectivity. It also contains utility features which allow importing and exporting of VPN configurations and profiles.
Vendor: Fortinet
Advisory: https://www.fortiguard.com/psirt/FG-IR-22-044
Product: FortiClientWindows VPN client
Vulnerable Versions: 6.0.0 through 6.0.10
- 6.2.0 through 6.2.9
- 6.4.0 through 6.4.7
- 7.0.0 through 7.0.3
Patched Versions: 7.0.4 or above
- 6.4.8 or above
Confirmed Vulnerable Platforms: Windows
Introduction to CVE-2022-26113
This post is the third and final post regarding vulnerabilities discovered when looking at the security of some popular VPN clients. In the first two posts we covered local privilege escalation and arbitrary file writes in Pritunl VPN Client and AWS VPN Client. This post covers an arbitrary file write as SYSTEM in the Fortinet FortiClient VPN client.
This issue differs a little from the first two posts in that it does not abuse dangerous directives in an OpenVPN configuration file, but instead uses an over privileged file write in config backup functionality of FortiClient.
FortiClient VPN Overview
FortiClient VPN allows normal users of the VPN Client to backup their VPN configuration. The backup file is written by FortiClient’s scheduler service running as SYSTEM, which calls the FCConfig.exe on the specified backup file.
Since the file path used to perform the backup to is only validated in the UI of the application, it is possible to bypass any permission checks and force the service to write to an arbitrary location, even if the user does not have permission to do so.
The user can control partial contents of the configuration backup, which means at the very least they could write a .bat script to an administrator’s startup directory as one method of privilege escalation.
Vulnerability Impact
This vulnerability allows an arbitrary file to be written anywhere on the system while controlling part of the contents. This can lead to privilege escalation in a number of ways, the most common being writing a script to a privileged user’s startup folder and then waiting for that user to log onto the system.
Technical Details
FortiClient is an Electron app that interacts with various services running in the background. A normal user is able to start and interact with the Electron UI of FortiClient.
It is possible to start the FortiClient application with the Electron debugging enabled and attach that to a debugger with Chrome.
C:\Program Files\Fortinet\FortiClient\FortiClient.exe --remote-debugging-port=9222
Now, opening Chrome with chrome://inspect will allow you to attach to the FortiClient process.


Here you can see the backup feature within the UI of FortiClient. The UI allows you to choose a backup file and checks to make sure the current user has permission to write to that file before allowing it to be selected. The selection is then disabled from editing.
Since we are debugging the UI we can obviously modify anything in the UI. To demonstrate this, we can use the JavaScript console to set the disabled property of the element to false.

Now the file path for the backup file can be modified to anything.

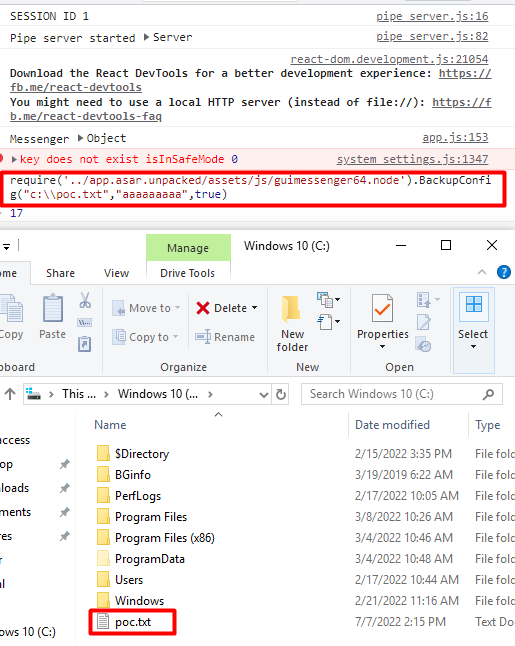
There are a number of ways you could bypass this using the debugger. After some digging the function to call the config backup service directly was found, allowing the function to be called from the JavaScript console, specifying an arbitrary path.
require('../app.asar.unpacked/assets/js/guimessenger64.node').BackupConfig("c:\\poc.txt","aaaaaaaaa",true)
Conclusion
Disclosure Timeline
Although FortiClient is not implemented in the same way as the other two VPN clients as a wrapper around OpenVPN, it was still possible to find a way to abuse the privileged services the client UI interacts with to write arbitrary files as SYSTEM.
We also want to thank the Fortinet team for working with us and getting this patched. As always, feel free to follow us on Twitter for more releases and blog posts: @RhinoSecurity, @daveysec
| 2/23/2022 | Issue reported to Fortinet |
| 2/24/2022 | Report acknowledged by Fortinet |
| 4/13/2022 | Rhino requests update on progress |
| 4/14/2022 | Fortinet updates issue has been fixed and assigned CVE, waiting on release |
| 6/6/2022 | Fortinet requests information for the advisory |
| 6/8/2022 | Fortinet informs Rhino the issue has been fixed and advisory published at https://www.fortiguard.com/psirt/FG-IR-22-044 |




