From Pentest to Pacu Module
During a recent AWS penetration test, the client was using a service I do not see very often: AWS Elastic Beanstalk (EBN). This is a service that makes it easy to deploy web applications without managing the underlying infrastructure. The client was using this service to host web apps to support their core services.
One of the first things I look for during an AWS penetration test is hardcoded secrets. I often discover credentials in services such as Lambda Functions, EC2 User Data, and Cloud Formation templates. These credentials provide a deeper foothold into the target environment, allowing me to elevate privileges or move laterally. Pacu simplifies this process–with just a few commands I can enumerate secrets from all these services.
After launching Pacu, I searched for modules related to “beanstalk” and found nothing to help with the engagement. I then spent the next few hours reading through AWS documentation to understand the API calls required for Elastic Beanstalk. Refusing to do this manually the next time, I started developing an Elastic Beanstalk Pacu module to save me (and you) hours on the next AWS penetration test.
This is the walkthrough of what I learned about Elastic Beanstalk and our new Pacu module to enumerate these cloud resources.
Elastic Beanstalk Service Details
AWS Elastic Beanstalk simplifies deploying and scaling applications by abstracting the underlying AWS infrastructure. When you create an Elastic Beanstalk environment, AWS provisions resources like EC2 instances, Load Balancers, and Auto Scaling groups on your behalf. Configuration of Beanstalk is done through a wizard in the AWS Console or via Infrastructure as Code (Terraform / CloudFormation).
Elastic Beanstalk organizes resources into ‘applications’ and ‘environments.’ You can think of the application as a folder for the project and the environment as a running copy of the app, configured a certain way (i.e., development, testing, production). This is admittedly confusing but important to understand.

This image shows the relationship between applications and environments. MyStore-dev and MyStore-prod are two separate environments within one application.
Environment properties allow developers to pass configuration details like database credentials or API keys directly into applications at runtime. Beanstalk also supports tagging so organizations can categorize environments. Depending on the organization’s use of tags, these may provide clues as to what to target or avoid (ie: a tag of “honeypot”).
The ability to set environment properties is convenient, but can lead to secret exposure if not configured properly.
Elastic Beanstalk Secret Exposure
One common misconfiguration is exposing sensitive information through environment properties and application source code. Elastic Beanstalk allows setting environment properties for each application environment – for example, database connection strings, API keys, or credentials. Similarly, the application’s source code (which Elastic Beanstalk bundles and stores in an S3 Bucket) may contain hardcoded secrets like API tokens or even AWS access keys. This misconfiguration is not limited to Beanstalk–the proper practice is to always store secrets in Secrets Manager rather than in environment properties or source code.
A leaked AWS access key or database password from an Elastic Beanstalk configuration can lead to privilege escalation, data compromise, or lateral movement within an AWS account. Even though Elastic Beanstalk abstracts away infrastructure management, the need to secure sensitive data and configurations is always the responsibility of the cloud customer.
Manual Enumeration of Elastic Beanstalk
During the penetration test, I began by using the AWS CLI commands DescribeApplications and DescribeEnvironments to list all Elastic Beanstalk applications in the account along with their associated environments. I then created a full inventory of deployments to identify sensitive Beanstalk deployments.
For each environment, I invoked DescribeConfigurationSettings which returned detailed configuration data (settings and environment properties). The environment properties contained numerous secrets–everything from AWS credentials to API Keys. These credentials allowed me to authenticate as other IAM principles and move laterally within the AWS account.
Finally, I ran DescribeApplicationVersions to identify the S3 bucket names and object keys where the source code was stored. I used the S3 API to download each source bundle locally, unzip it, and perform static review of the underlying code. I discovered more hardcoded credentials in the code which led to privilege escalation.
What took me hours of reading AWS documentation and manually looking for secrets can now be done in minutes with our new Pacu module.
Introducing ‘elasticbeanstalk__enum’ Pacu Module
To uncover these risks, we have developed a new Pacu module called ‘elasticbeanstalk__enum.’ This module automates the manual process a penetration tester would otherwise perform. At a high level, ‘elasticbeanstalk__enum’ does the following:
- Enumerates Elastic Beanstalk Applications and Environments
- Gathers Configuration Settings and Tags
- Downloads Application Source Code
- Scans for Secrets
Module Details
- Enumerates Elastic Beanstalk Applications and Environments: It lists all Elastic Beanstalk applications in the target AWS account and their associated environments. This gives an immediate inventory of what apps exist and how many environments each has. Applications can contain multiple environments, such as development, staging, and production.
- Gathers Configuration Options and Tags: For each environment, the module retrieves configuration options, including environment properties and configuration details. Any tags applied to Elastic Beanstalk resources are also collected. Tags can sometimes hint at environmental purpose or owner, which can be useful in an assessment.
- Downloads Application Source Code (Optional): The module attempts to download the source bundle for each application version deployed in Beanstalk. These bundles are stored as .zip files in an S3 Bucket. The module will locate the S3 bucket and download the app source code for static analysis. Downloading source code is optional and will only run if the –source flag is specified.
- Scanning for Secrets: Finally, the module uses Pacu’s Secrets Finder library to scan the retrieved environment variables and source code for secret patterns such as AWS Secret Keys, database connection strings, API keys, private SSH/X.509 keys, Beanstalk Config passwords, and other sensitive strings.
Getting Started with ‘elasticbeanstalk__enum’
After importing AWS keys into Pacu, you can retrieve more information on this module:
help elasticbeanstalk__enum
The module provides the following options. If an option is not specified, it will attempt to run all of the options (except for downloading source code) in the targeted account.
- Region: Comma-separated AWS regions, e.g., “us-east-1”. Defaults to all session regions.
- Applications: Enumerate all Beanstalk applications.
- Environments: Enumerate all Beanstalk environments for each application.
- Config: Enumerate all configuration settings (including environment variables).
- Tags: Enumerate resource tags for all environments.
- Source (Optional): Download the deployed app source code for further review.
Running the module with these options is simple:
run elasticbeanstalk__enum –region us-east-1
This will enumerate all applications, environments, configurations, and tags. Any secrets discovered by Pacu will be green on the terminal and downloaded for verification.
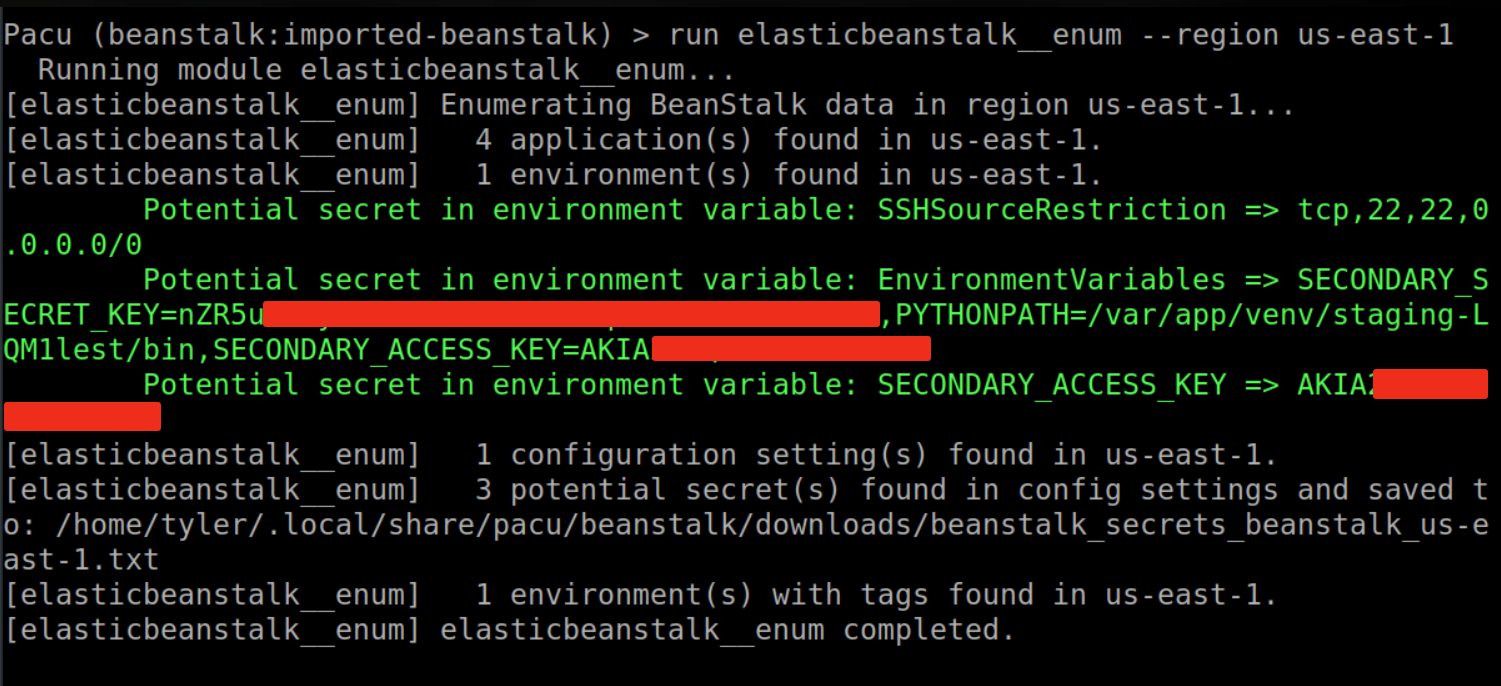
This image shows the output of running the module with default options.
The module will output “MODULE SUMMARY” at the end to provide an overview of the Elastic Beanstalk instances:

The MODULE SUMMARY
Output from the module can be retrieved from within the Pacu session. This provides an easy way to check the Beanstalk configurations from within Pacu (i.e. Environment Names, Application Names, URLs) with the following command:
data elasticbeanstalk
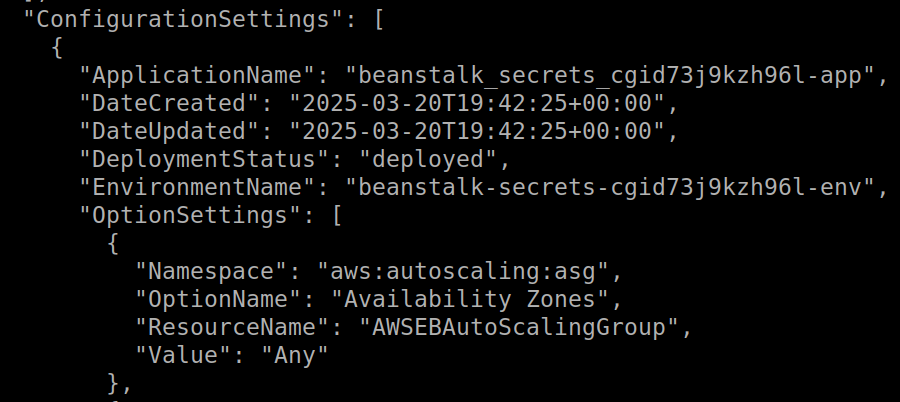
This image shows the output of the “data elasticbeanstalk” command in Pacu.
Hands-On: New Beanstalk CloudGoat Scenario
To help you get practice with this new module and learn common AWS misconfigurations we have created a new CloudGoat scenario named beanstalk_secrets.
In the scenario, you are provided with low-privileged AWS credentials, tasked with enumerating and exploiting the Elastic Beanstalk environment, and elevating your privileges to capture the final flag.
Conclusion
Elastic Beanstalk simplifies application deployment, but also expands the attack surface if secrets are not stored properly. This module will save you the time of reading through AWS documentation and trying to figure out just the right flag to search for secrets. Using Pacu to automate the process ensures all secrets are discovered, verified, and reported to the client.
Twitter: https://twitter.com/rhinosecurity
LinkedIn: https://www.linkedin.com/company/rhino-security-labs/
Discord: https://discord.gg/vTWRkdPxk2